The combination of:
- Where a device is coming from
- Where a device is going
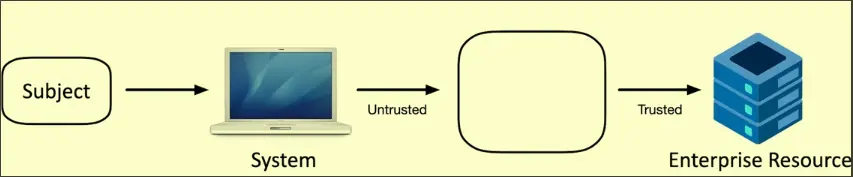 These security zones are enforced with PEP
Allows for Network Segmentation, DLP, data protection, Access Control. System Monitoring, Isolation, Security Compliance, Incident Containment, operational efficiency, Defense In Depth
These security zones are enforced with PEP
Allows for Network Segmentation, DLP, data protection, Access Control. System Monitoring, Isolation, Security Compliance, Incident Containment, operational efficiency, Defense In Depth
Zone Permissions
Devices within these zones will be given certain permissions.
- Restrictive permissions from those that are accessing from an untrusted network
- Trusted permissions for devices within the office