Challenge
 https://cybersharing.net/s/4a47f2774279abd1
https://cybersharing.net/s/4a47f2774279abd1
Initial Recon
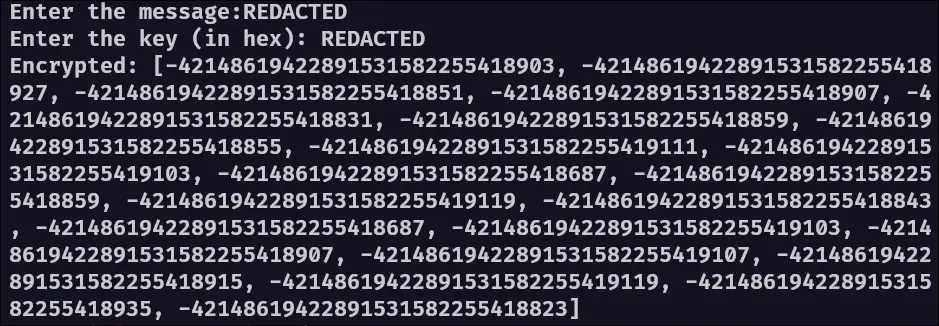 The output file contains an encrypted list of 21 elements.
The output file contains an encrypted list of 21 elements.
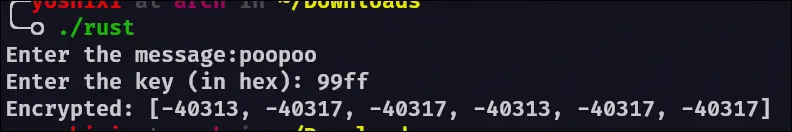 If we try to run the file normally, we see that the size of the list is equivalent to the number of characters you input.
We can assume that the flag will be 21 characters long then
If we try to run the file normally, we see that the size of the list is equivalent to the number of characters you input.
We can assume that the flag will be 21 characters long then
Solution
https://vaktibabat.github.io/posts/ictf_2024/ Decompiler with Ghidra.
main()
- Takes input through stdin
- Sends input to encrypt()
encrypt() function
- create an
encryptedvector - iterate over all bytes of user’s input message
- next element in the iterator is put into
0Var1 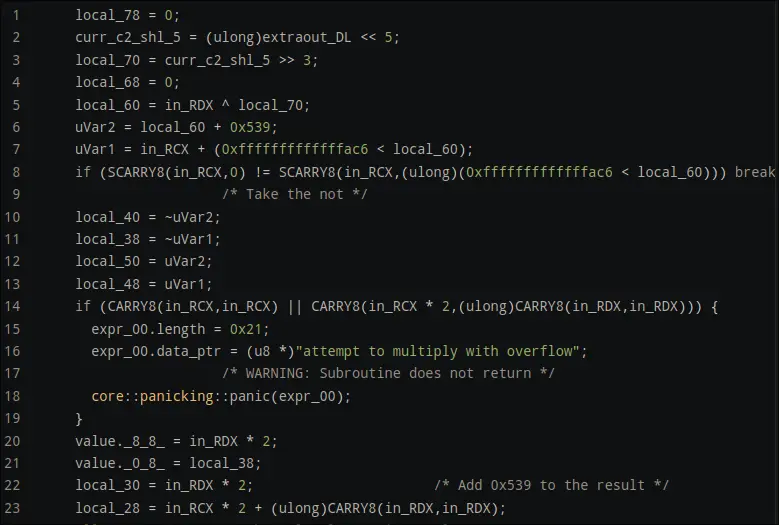 this section of the code likely handles the encryption, as it pushes to the
this section of the code likely handles the encryption, as it pushes to the encryptedvector at the end
- next element in the iterator is put into
encryptedvector is printed out
Using GDB to investigate
For the encryption portion: Input:
- message is
ABCDE - key is
0x1234
- some local variables are moved into
rcxandrax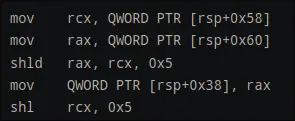
- stepping 2 instructions shows the values of rax and rcx
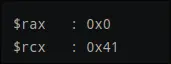 rcx contains byte of message (
rcx contains byte of message (Ain this case) rax contains0 - 5th instructions shift
rcxto the left 5 times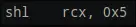
- later instructions involve another shift
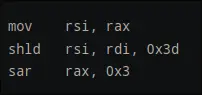
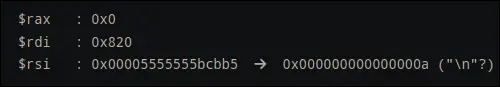 inspecting this:
inspecting this:
- rax is 0
- rdi is the (current byte << 2
- rsi is a pointer to a newline
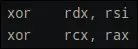
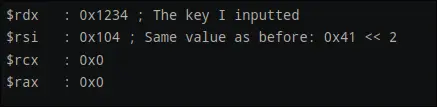 so far what was done was:
b = a ^ key
so far what was done was:
b = a ^ key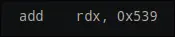 b = a ^ key + 0x539
b = a ^ key + 0x539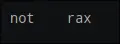 b = -(a ^ key + 0x539)
so the algorithm is:
b = -(a ^ key + 0x539)
so the algorithm is:
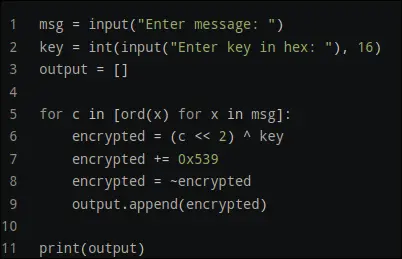 The script to solve this is:
The script to solve this is:
for y in output_of_flag:
x = ~y
x -= 0x539
x ^= key
x = x >> 2
flag.append(x)
print("".join([chr(c) for c in flag]))ictf{ru57_r3v_7f4d3a}