The practice of finding hidden data from digital traces like:
- Logs
- Memory dumps
- Packet dumps
- Images
- Audio
Concepts
Process
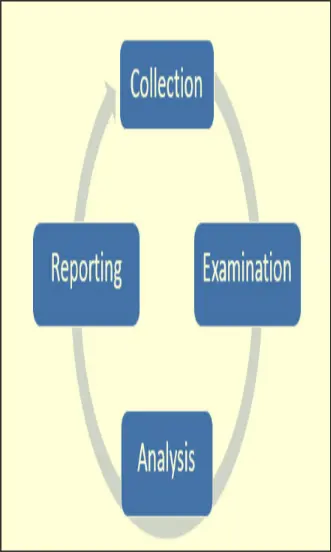
Collection
Collect evidence from the attack
Examination
- Data is hashed
- Investigation carried out with forensics tool
Analysis
- Data analyzed using legal methods
- Data transformed into evidence
Reporting
- Forensics team creates report that can be presented as legal evidence