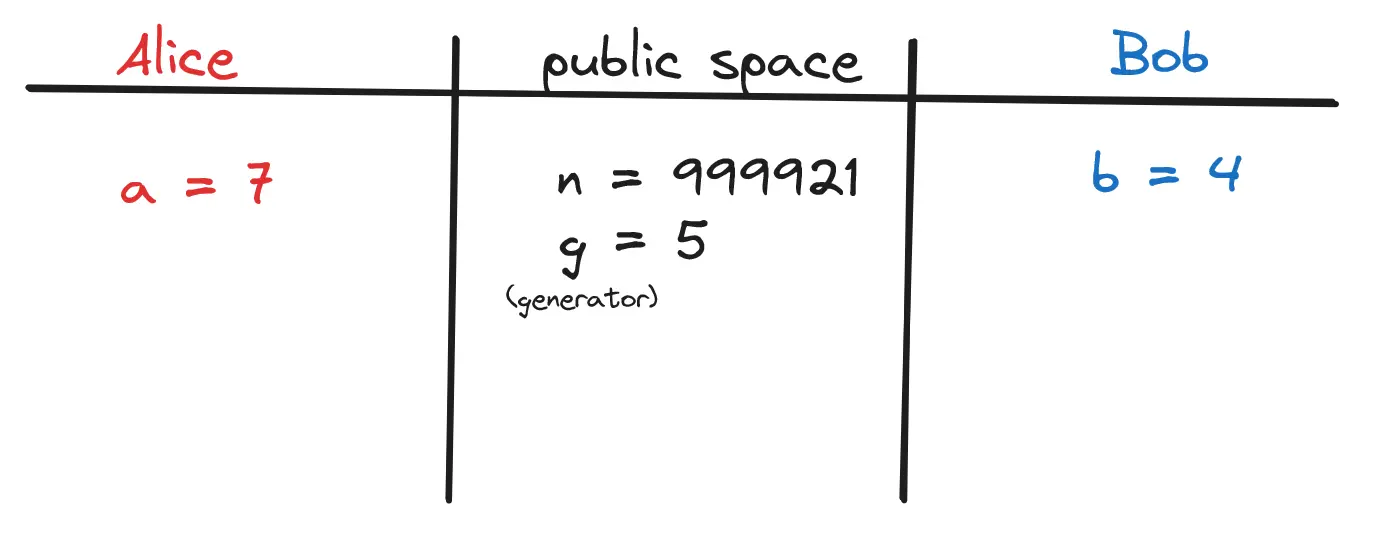
A method used in End to End Encryption to generate the shared key through sharing public variables, combining them with private variables and ending up with both users having the same result.
Process
- Alice has private key , Bob has private key , public variables and are stored.
is a very small prime number
is a very big prime number
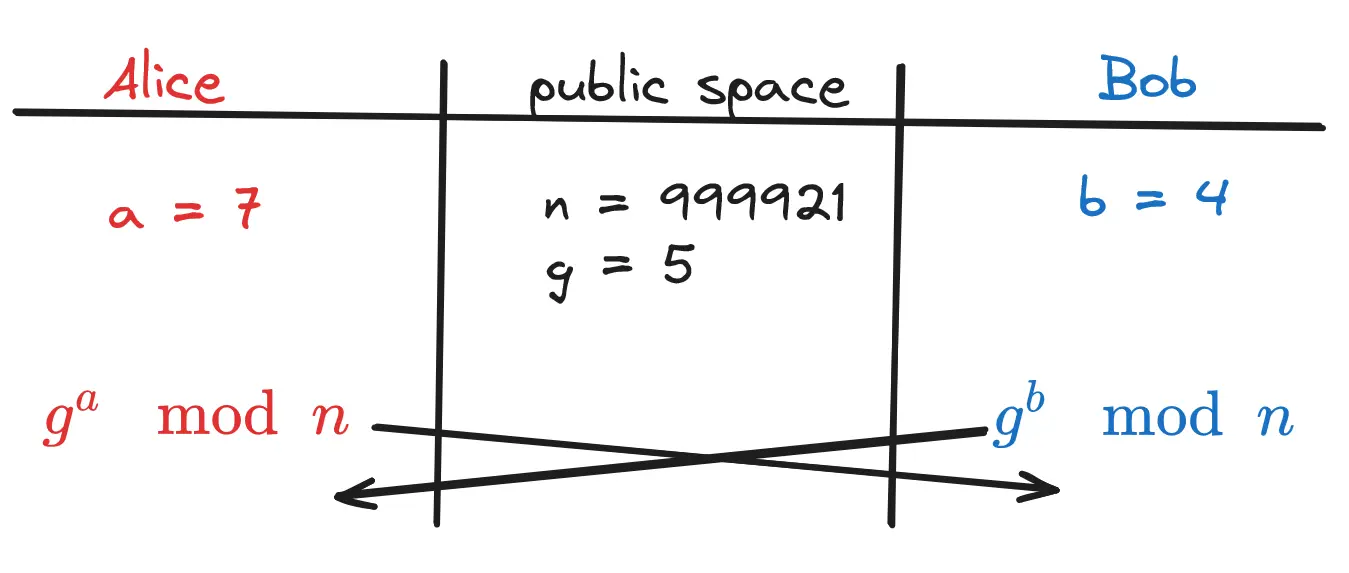
- Bob and Alice each calculate and then share them with eachother.
- Each user receives the other discrete logarithm key from the other and then raises it by their own private key
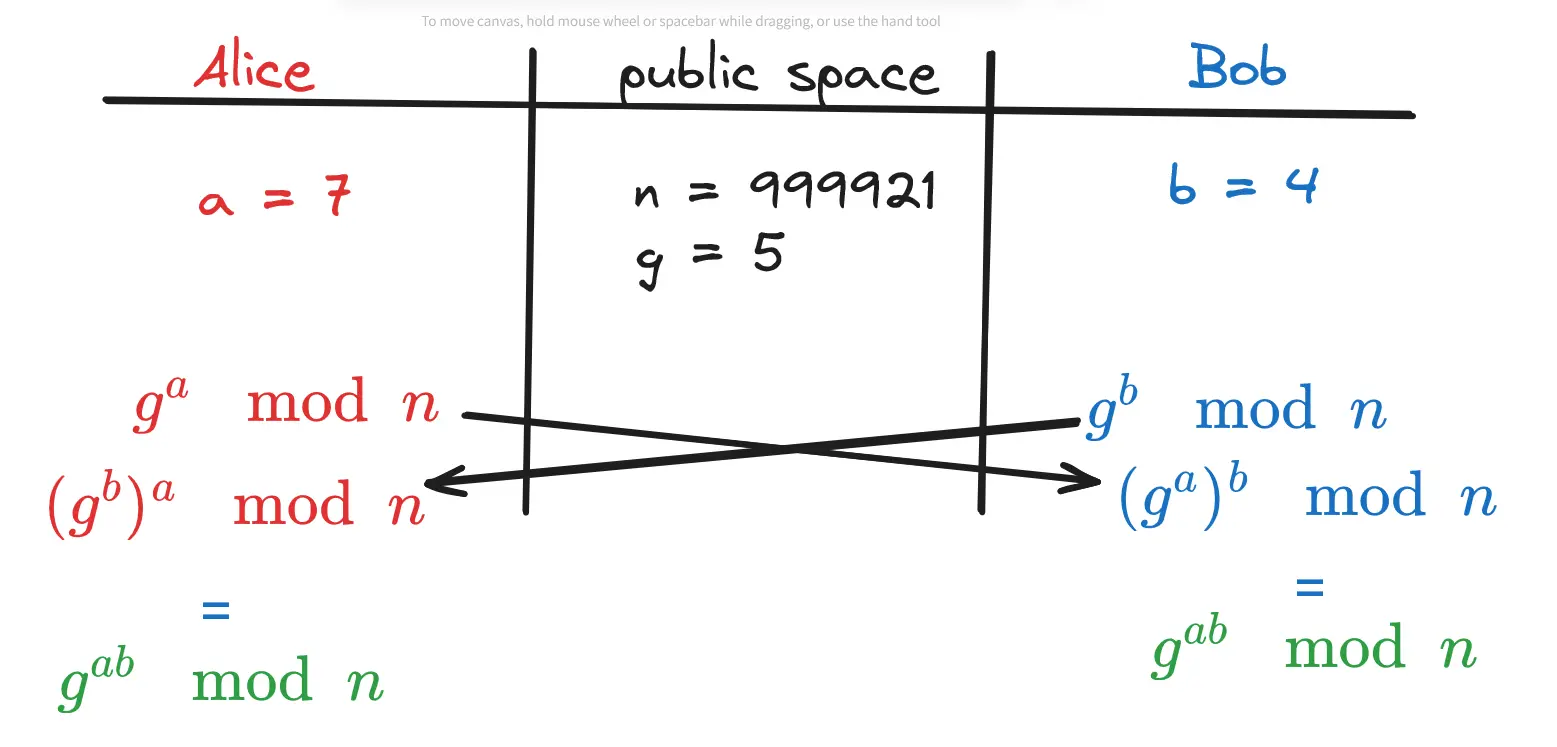 this results in both users having the same symmetric key
this results in both users having the same symmetric key
Decryption
This is based off the Discrete Logarithm Problem that can be solved with: