A MITM setup attack that has a third party device spoof the ARP response to change the ARP cache of a target device.
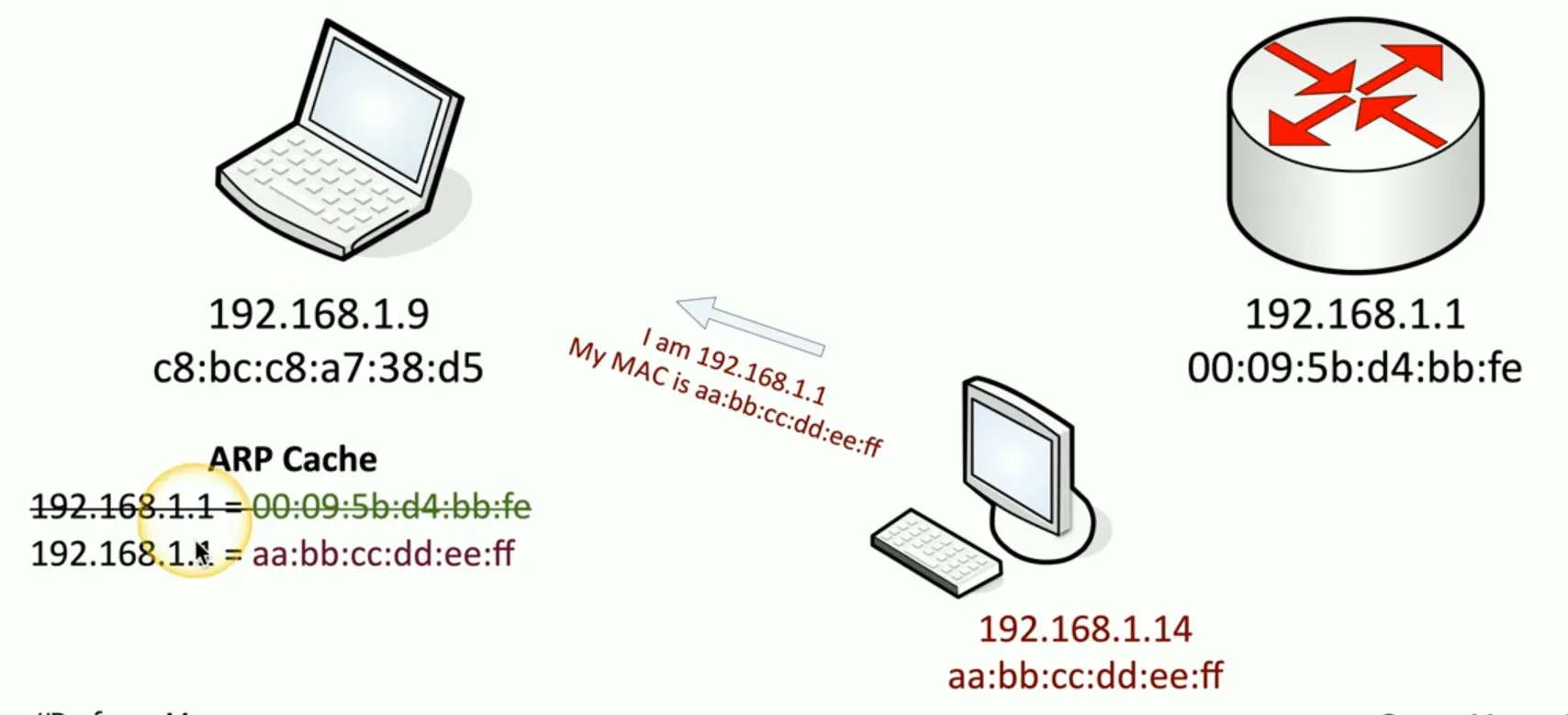 The attacker will then do the same attack to the router, thereby allowing the attacker device to sit between the traffic of the two devices.
The attacker will then do the same attack to the router, thereby allowing the attacker device to sit between the traffic of the two devices.