Recon

- The string buffer size is 200 characters
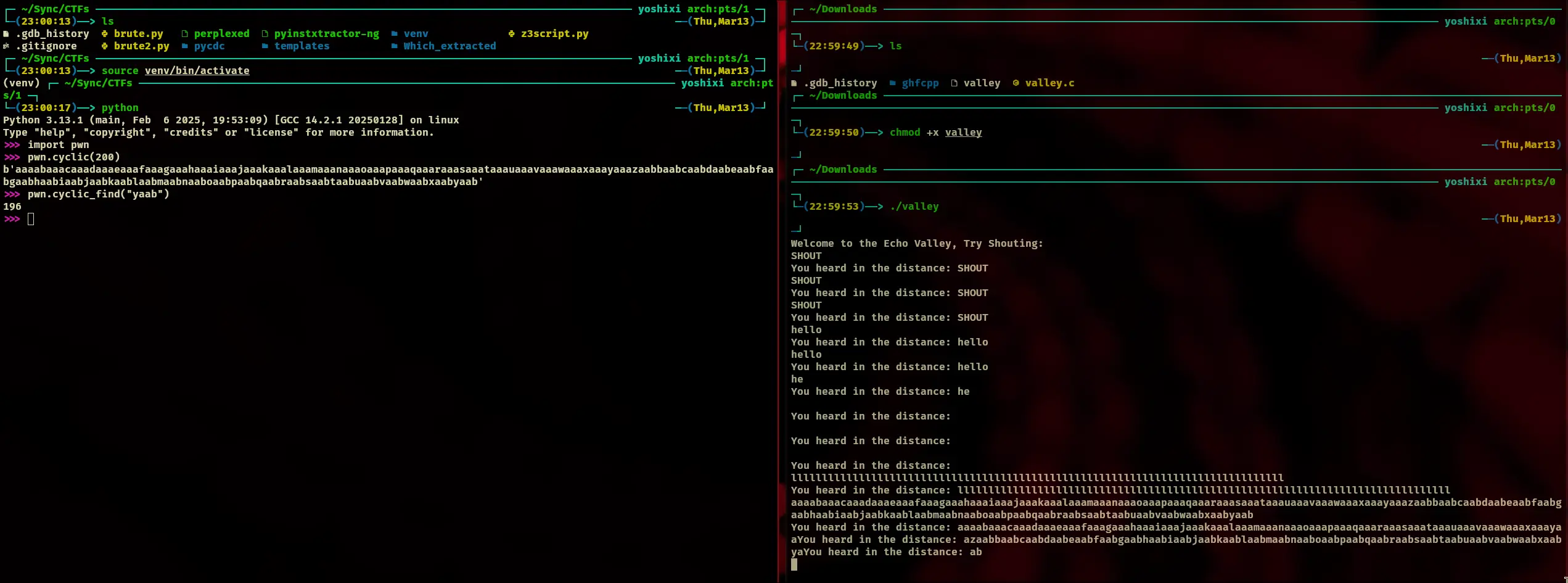
- Jacky told me there is a format string vulnerability which it does have
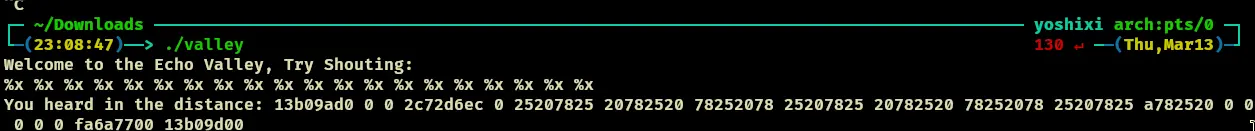
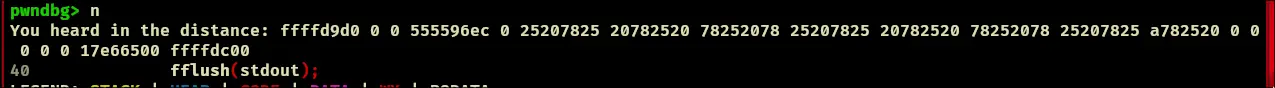 , and lets see what the corresponding output is in the debugger? Couldnt find this…
, and lets see what the corresponding output is in the debugger? Couldnt find this…- Note that we want to change the return address to the return address that points to
print_flag()
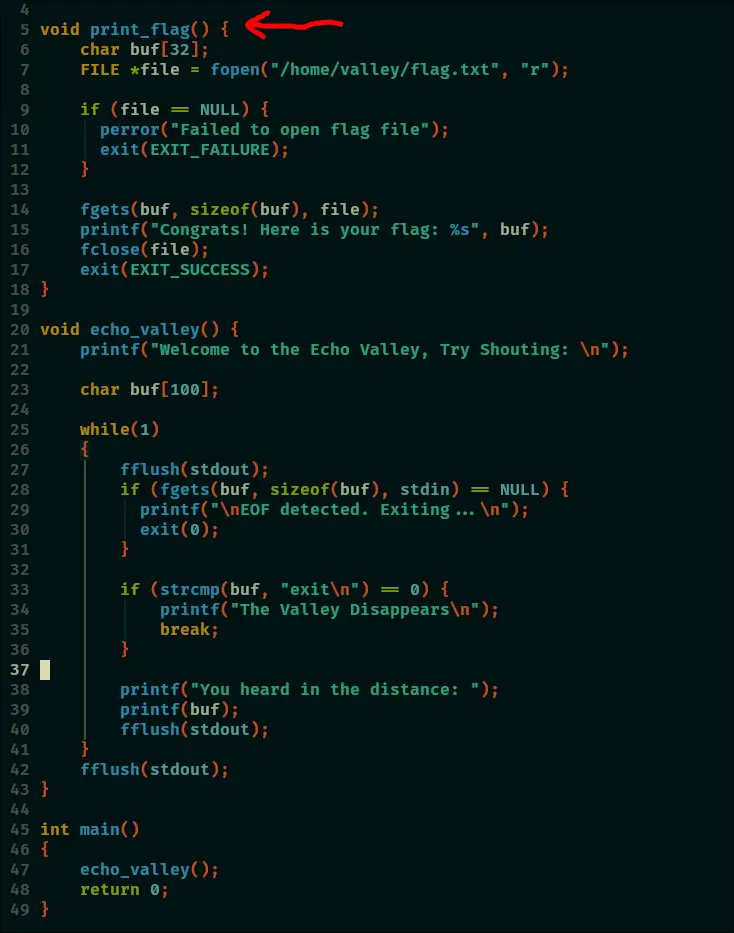
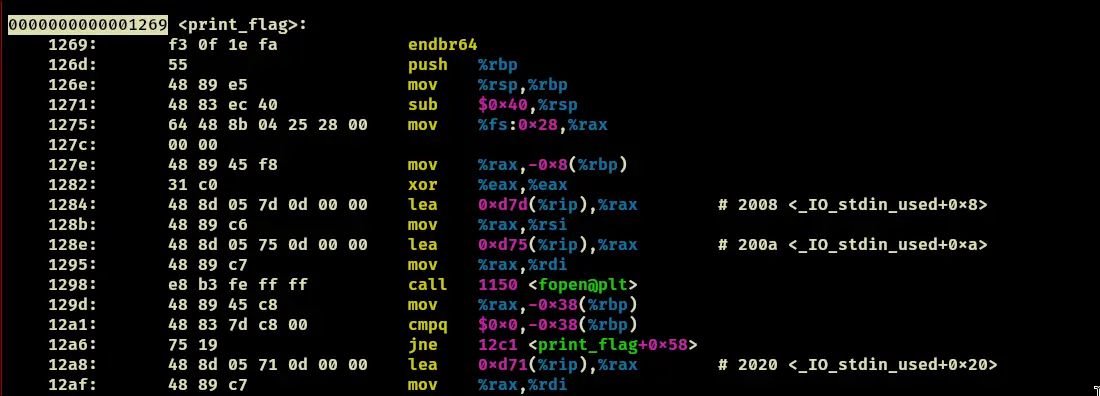
- The relative offset for print_flag() is:
- The main-function body is seen in the 6th item on the stack when we start running
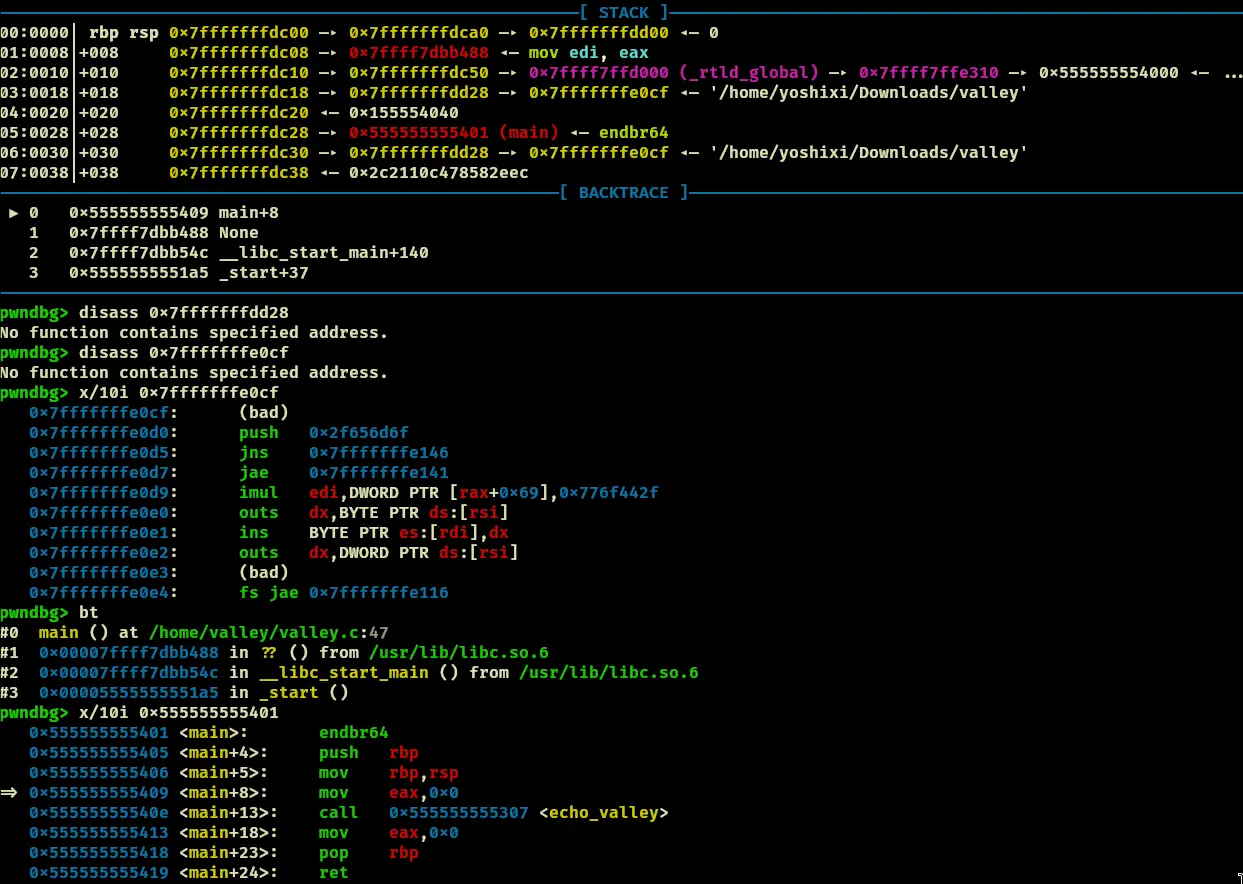
What we need to do
- Leak the base address for print_flag(), the offset for print_flag() is
0x1269
- Modify the return address with Format String Exploitation to be the address where print_flag() is located
- Leak the Stack Canary and then



 , and lets see what the corresponding output is in the debugger? Couldnt find this…
, and lets see what the corresponding output is in the debugger? Couldnt find this…

