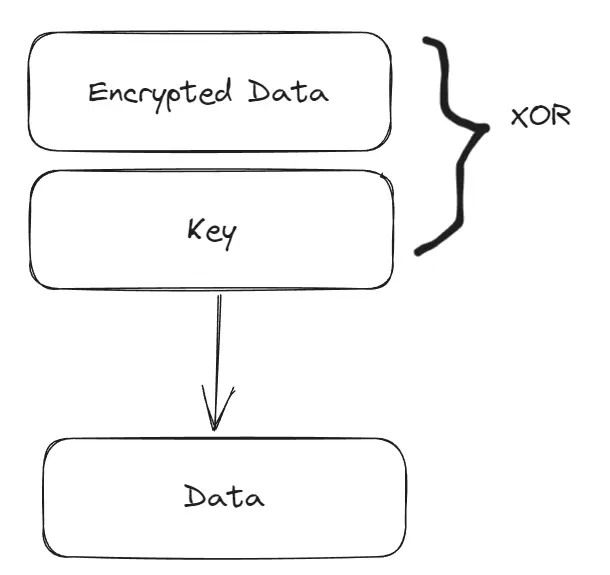
One of the most common bases for encryption. It is uniformly random, after encryption, making it a very good one-time-pad.
The Process
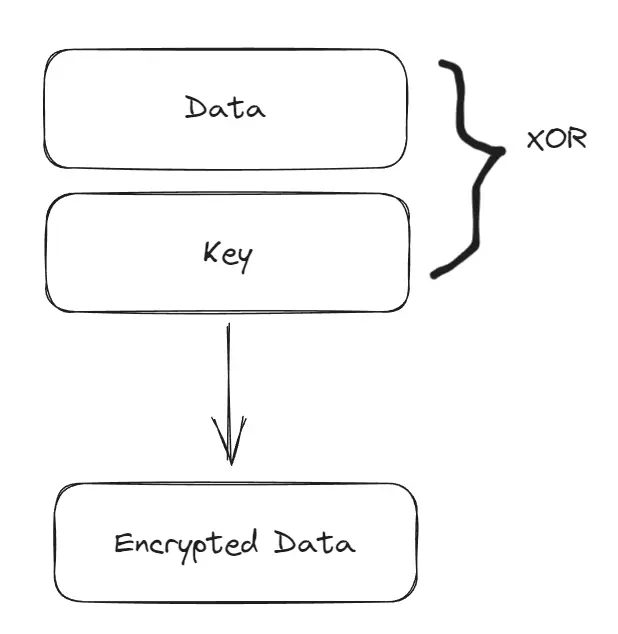
These types of encryptions require only:
- a key
- original data
They will be XOR’d together, making an encrypted data
 If you want it back, then just XOR with the same key again
If you want it back, then just XOR with the same key again