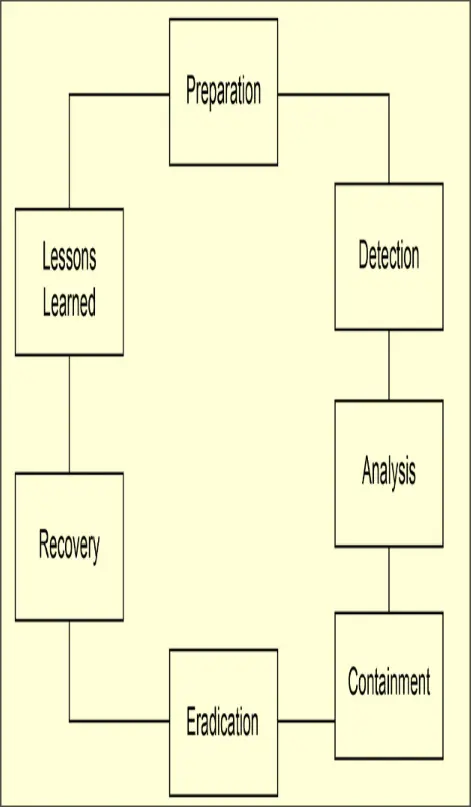
Process
Preparation
Detection
- Setup EDR on network endpoints
- Setup IDS
- Set up logging with a Syslog server
- Setup SIEM
Analysis
Containment
- Isolate and Quarantine affected systems
- Compromised user accounts and credentials should be disabled
- Volatile evidence like running processes, network connection should be collected for future analysis
- Grab a sample of malware and isolate it
Eradication
- Destroy the root cause of incident. If its malware, then purge it
- Delete infected files
- Patching
- Protect environment against future attacks
Recovery
- Restore operations to a normal state
- Data restoration
- Devices brought back online
- Reach the Recovery Point Objective as early as possible
Lessons Learned
- Conduct a post-incident analysis
