A Flutter reverse engineering tool that can be used to hook and intercept function calls. You require a Rooted android phone to use frida, or an android emulator with adb
Client Installation
Windows
pip install frida-tools
The library is located at <pythonfolder>/Lib/site-packages/frida-tools
The example scripts are located at: <pythonfolder>/Scripts/
Arch
sudo pacman -S python-frida python-frida-tools
Server Installation
AVD Setup
- Check the CPU architecture of the AVD device
- Download the correct server release off https://github.com/frida/frida/releases
- Unzip the xz file
adb push <fridaserverfile> /data/local/tmp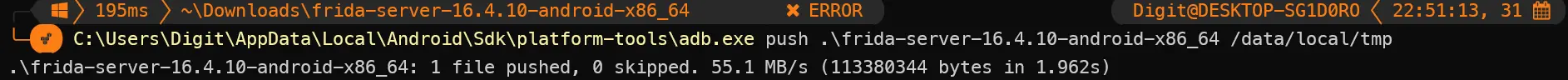
adb shellsucd /data/local/tmpchmod 755 <fridaserverfile>./<fridaserver> &
Starting Frida
- Use Blutter to create
blutter_frida.js - Modify
blutter_frida.jsto remove the warning and to modify the hook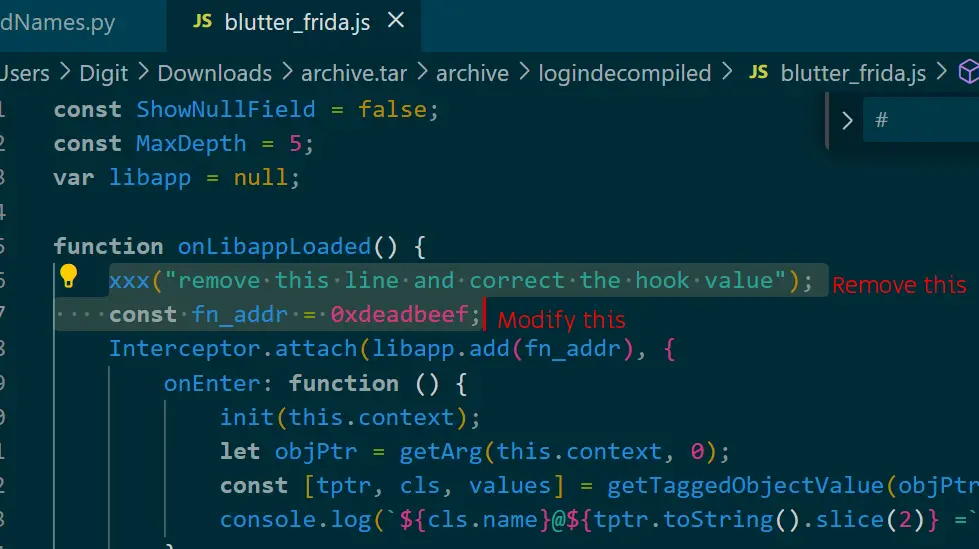
Emulated Device
- Run the app on the emulator
frida-ps -Uato view appname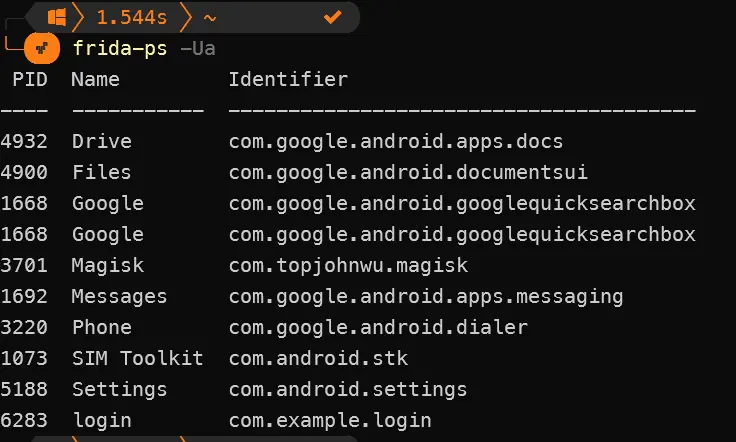
frida -U <appname> -l blutter_frida.js
Tools
frida-ps -U- show all running processesfrida-ps -Ua- show all running applicationsfrida-ps -Uia- show all running and not running applicationsfrida -U -f <app>.apk -l <script>.js
Frida Commands
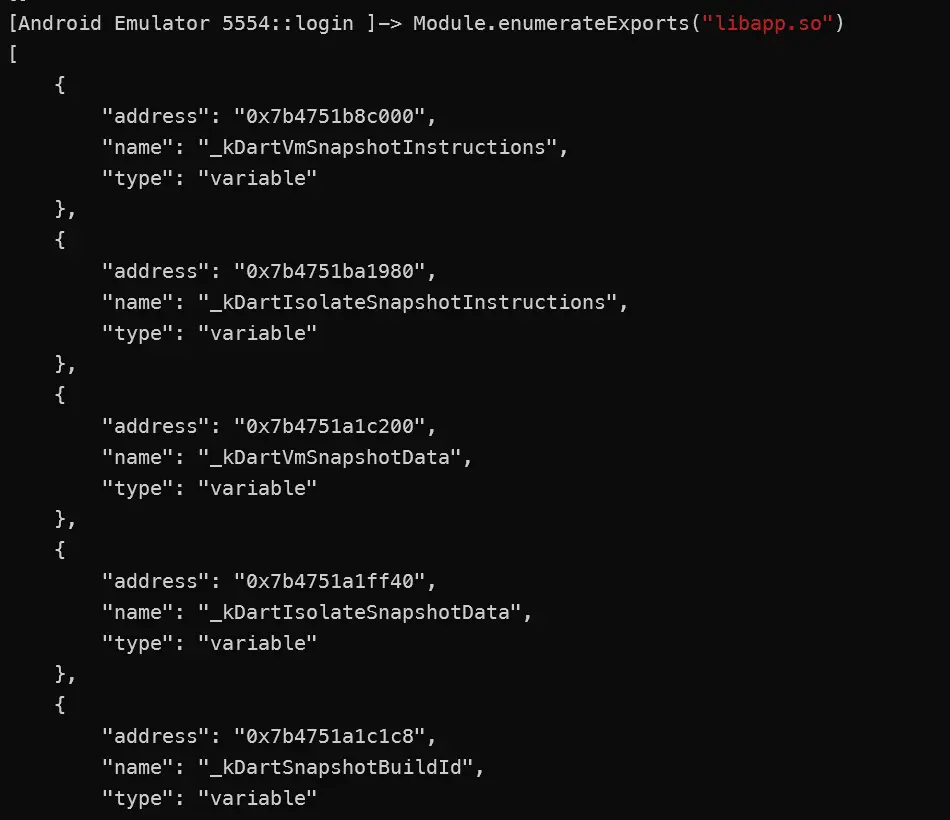
Module.enumerateExports("libapp.so")- prints all the exported functions and variables along with their address in memory