- run FLOSS on the binary, and we find that it is packed with UPX packer
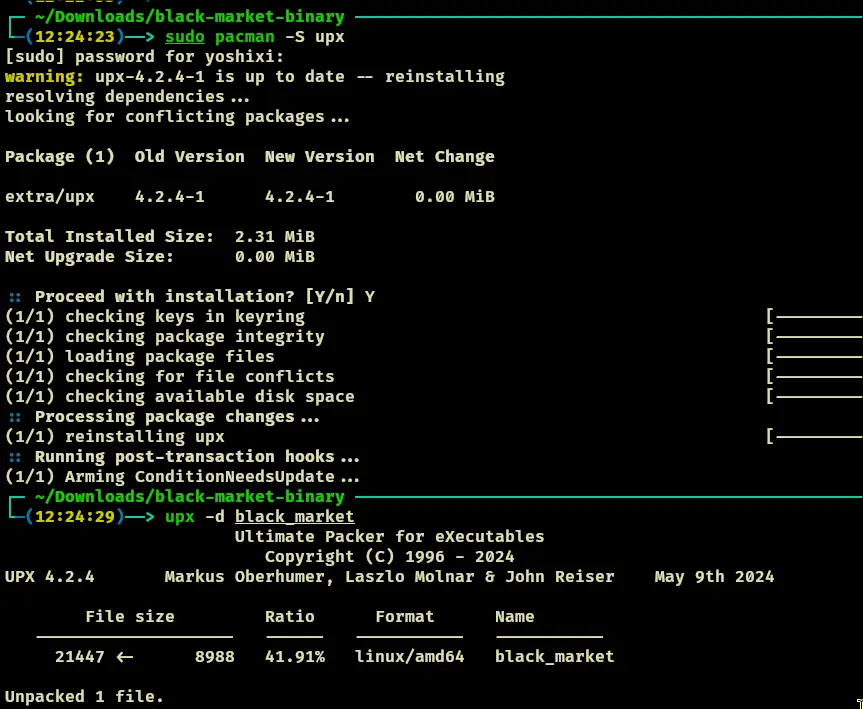
- Obviously, there is a encryption algorithm within this code, and in fact, it is scrambling this flag
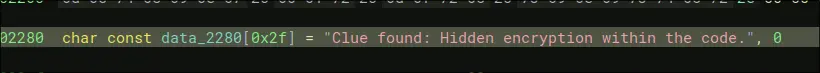
- There is this decrypt files program that seems to output the same things
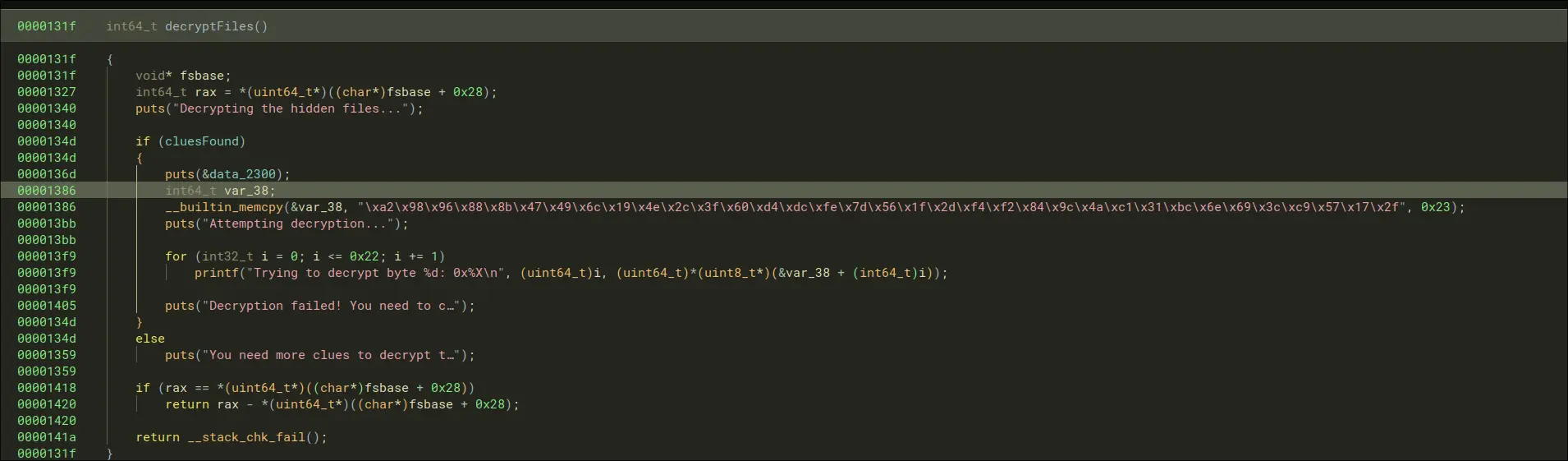
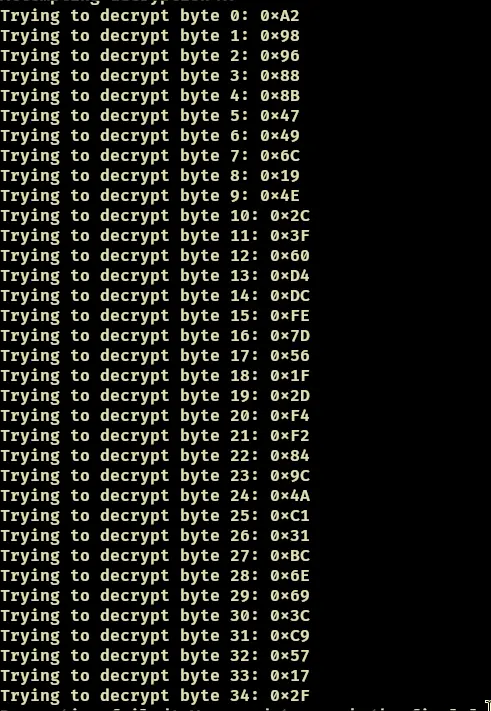 Looks pretty useless to me.
Looks pretty useless to me.
- Lets use GDB.
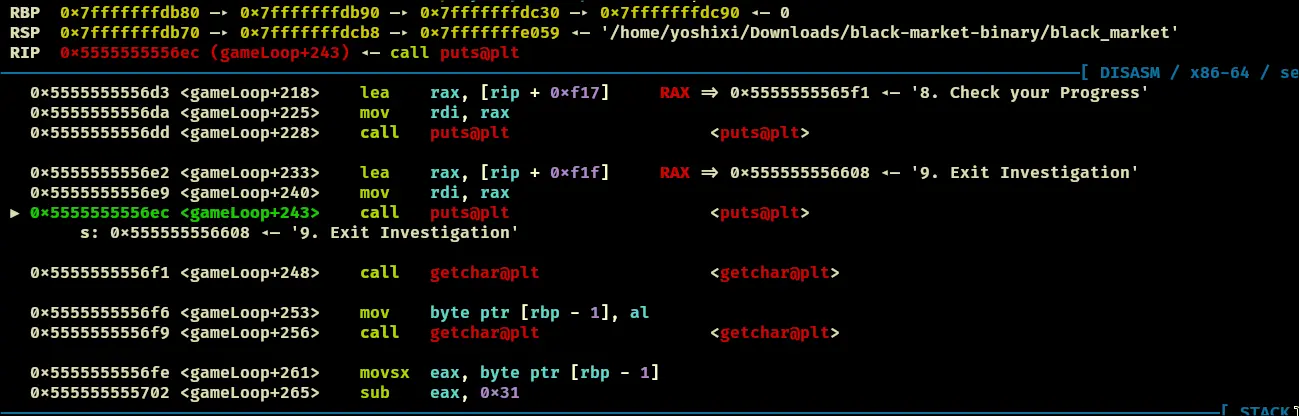
- Set a breakpoint anywhere after the gameloop is ran. I set mine here:
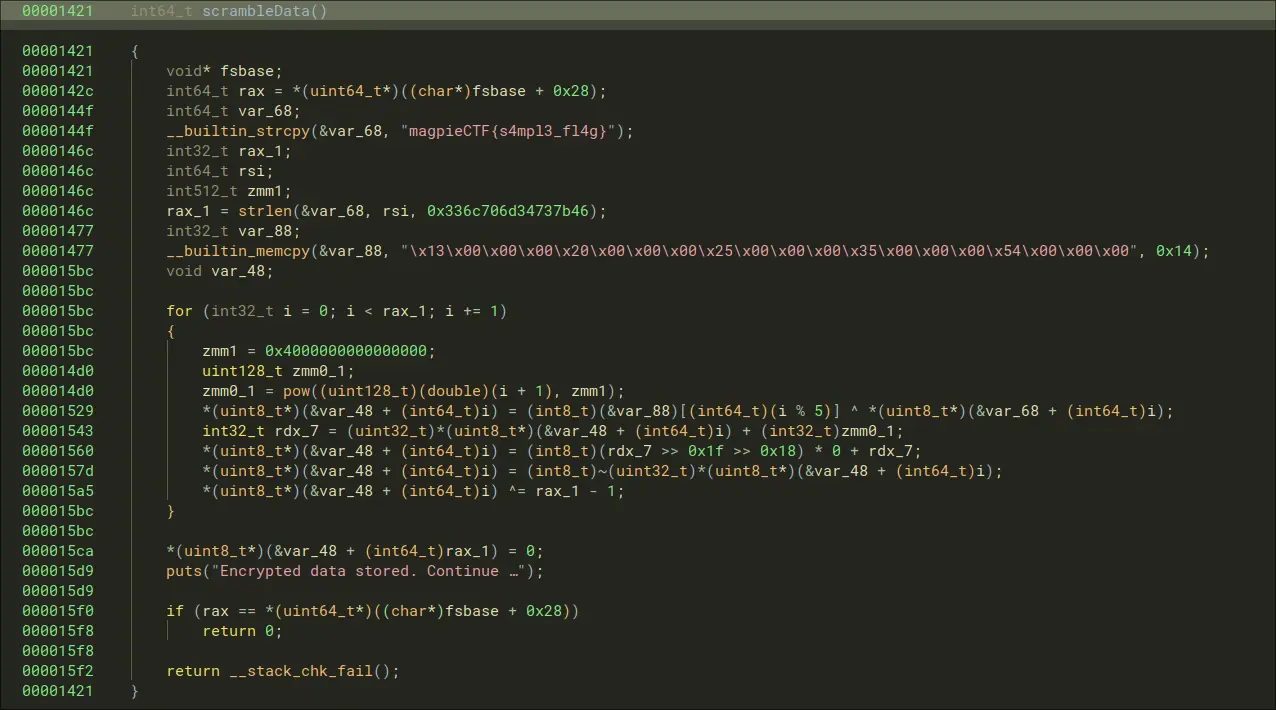
- Set another breakpoint at scrambledata function
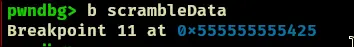
- lets jump to the scrambledata function.
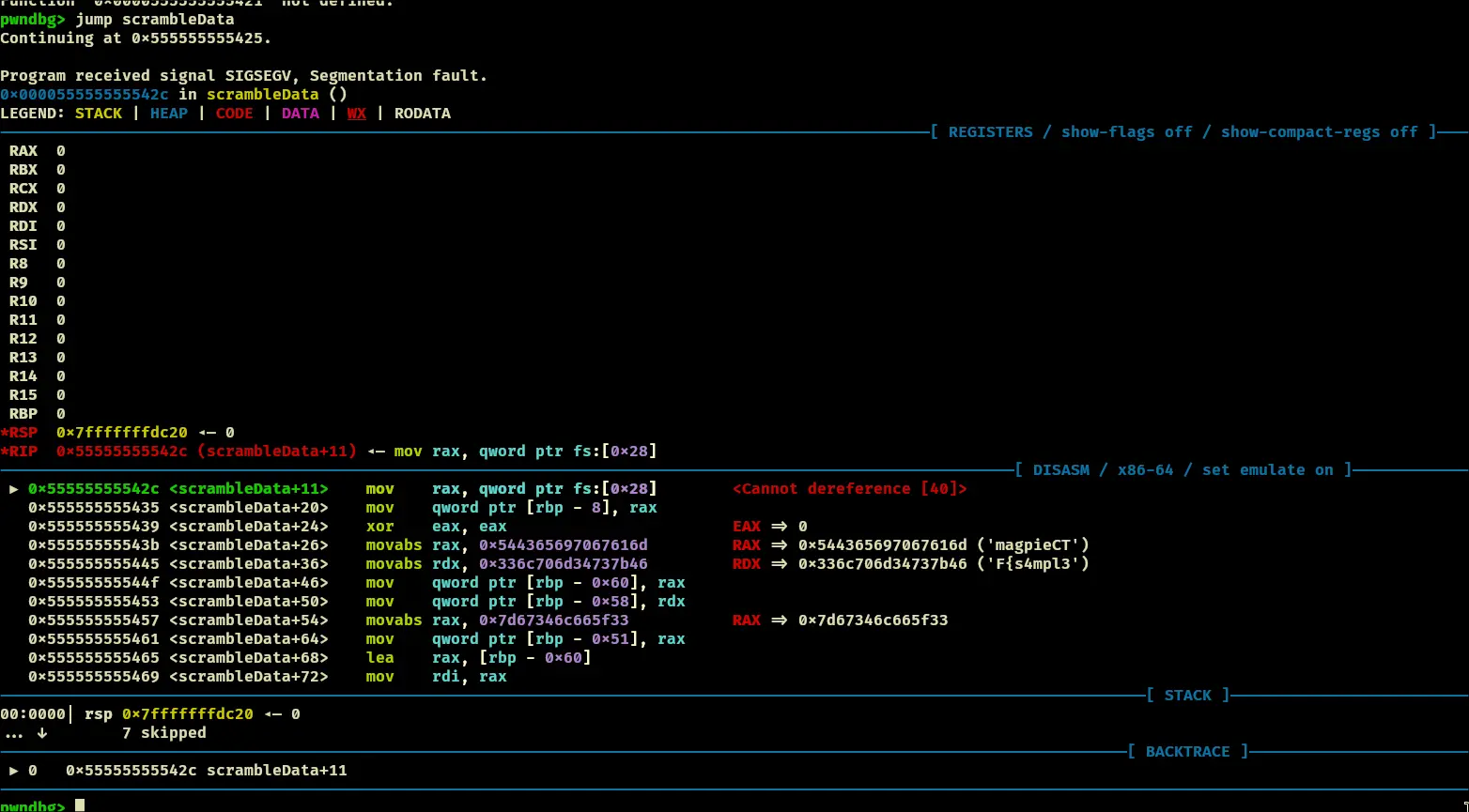
- Takes the strlen of
magpieCTF{s4mpl3_fl4g} which is 22 or 0x16
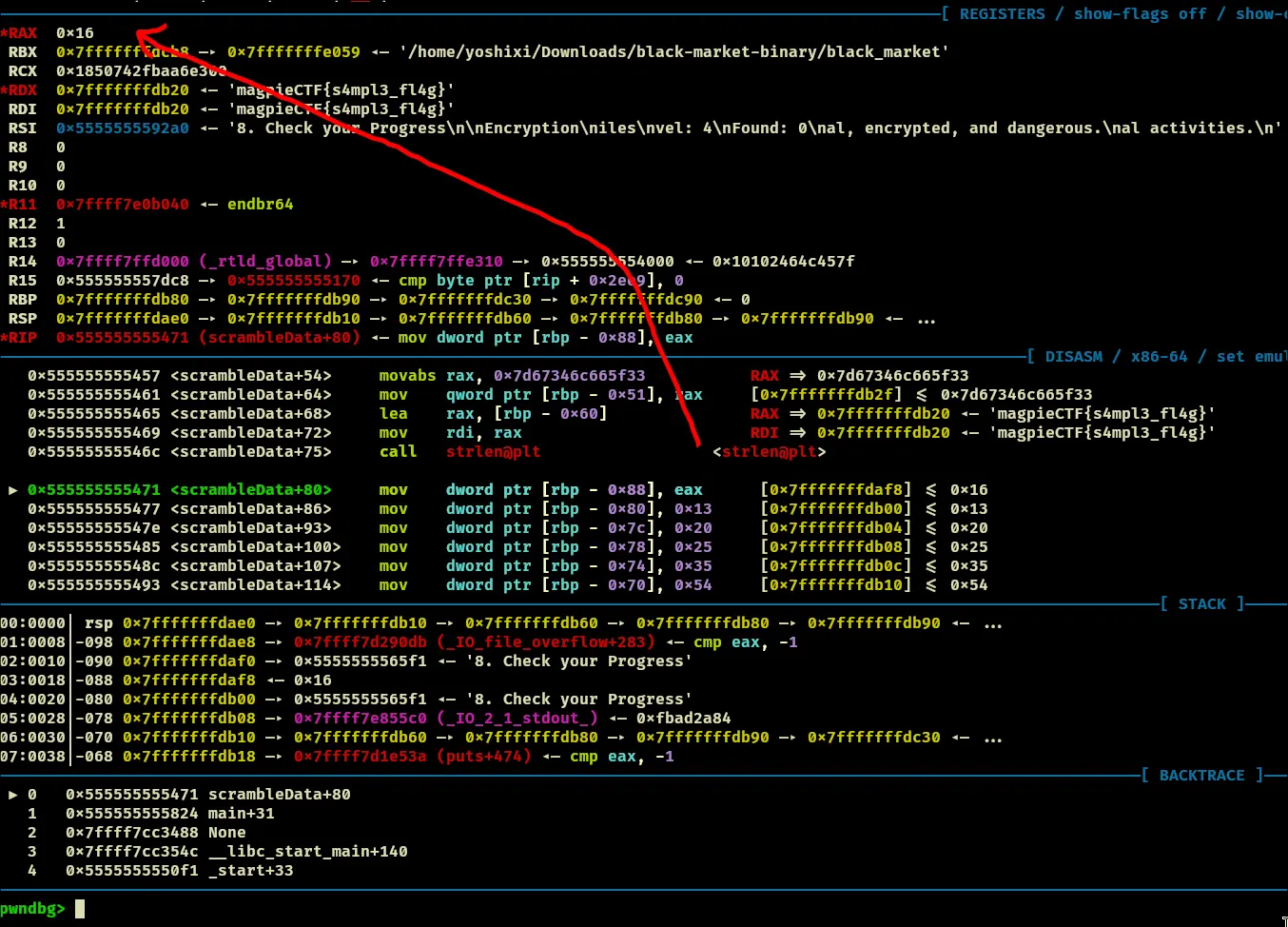
- Afterwards, enter a loop that goes 22 times, after that loop with all the operations, you land here:
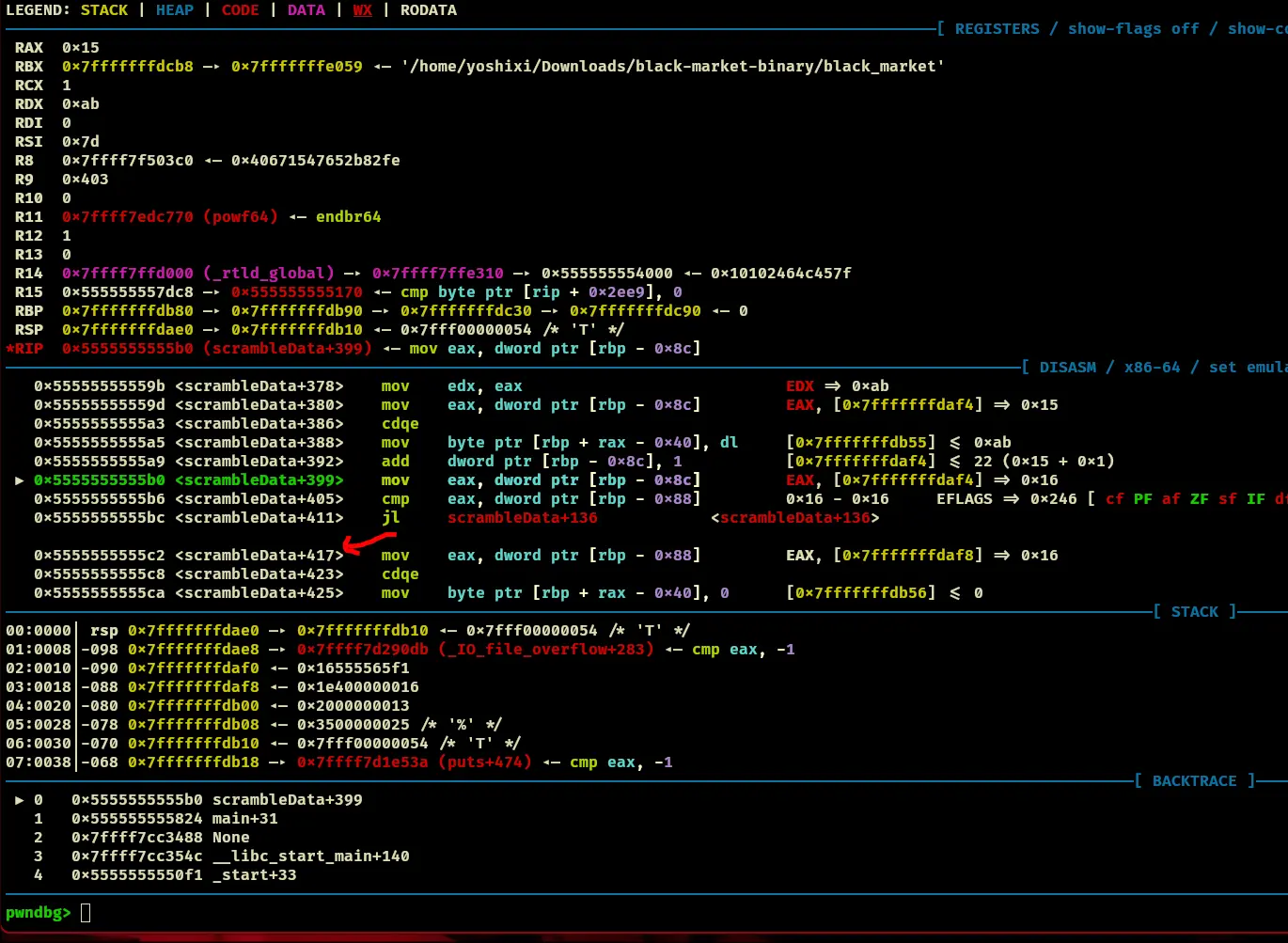





 Looks pretty useless to me.
Looks pretty useless to me.



