Human trust is flawed. Assume the attacker is already inside the system.
Principles
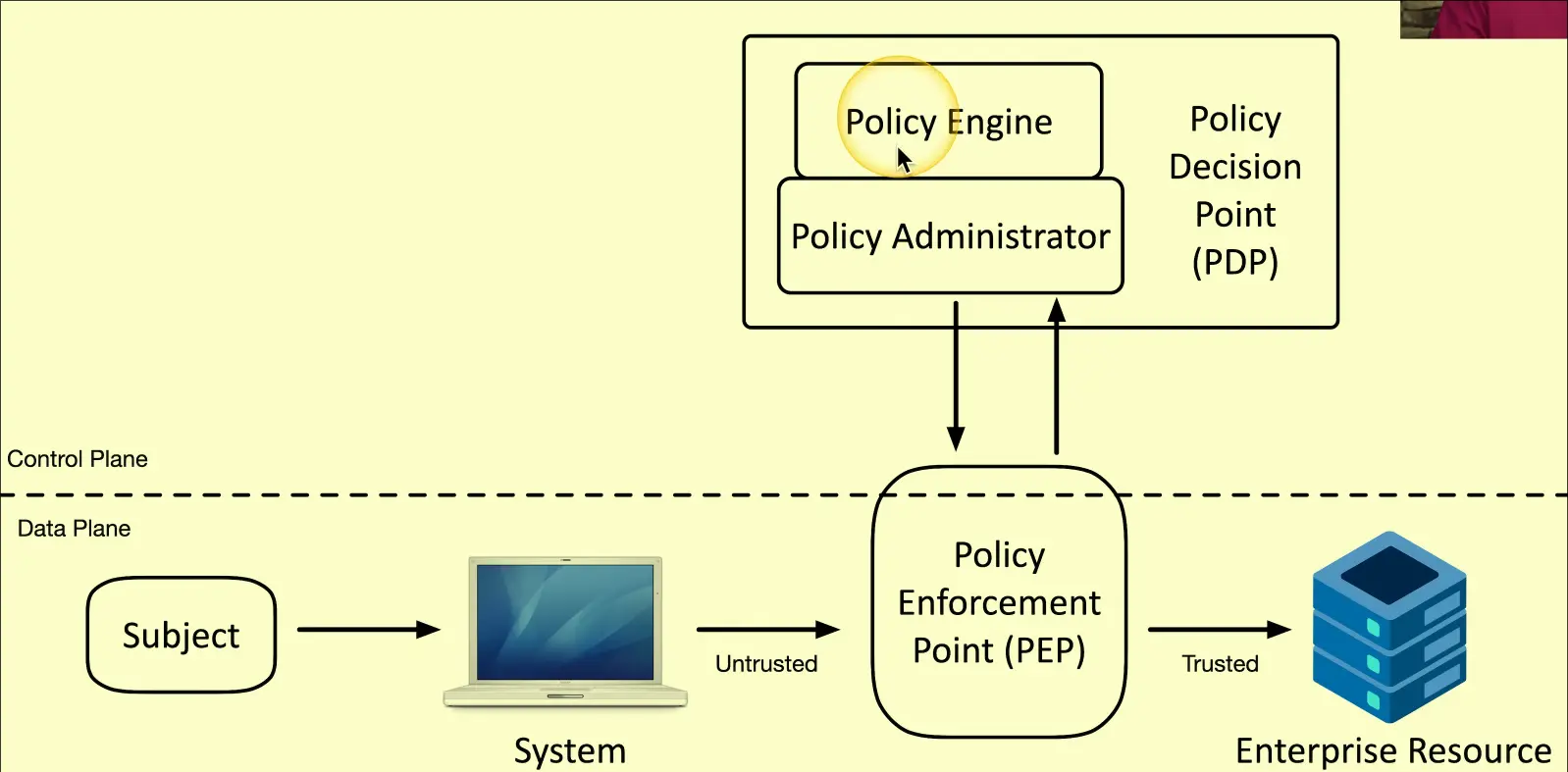
- Never trust, always verify. Every connection attempt should be authenticated and authorized. Use Adaptive Identity
- Implement Principle of Least Privilege. Give them the least amount of access for them to do their job
- Assume breach. Micro segmentation through Planes of Operation and PEP to allow traffic only from specific sources
Concepts
- Principle of Least Privilege
- Adaptive Identity
- Planes of Operation
- Security Zone
- PEP
- Threat Scope Reduction