- Authenticate users
- Authorization what resources they can access
- Log all actions for Accountability
- Attestation for ensuring compliance
Implementations
AAA Servers
These servers sit on a LAN to provide AAA resources.
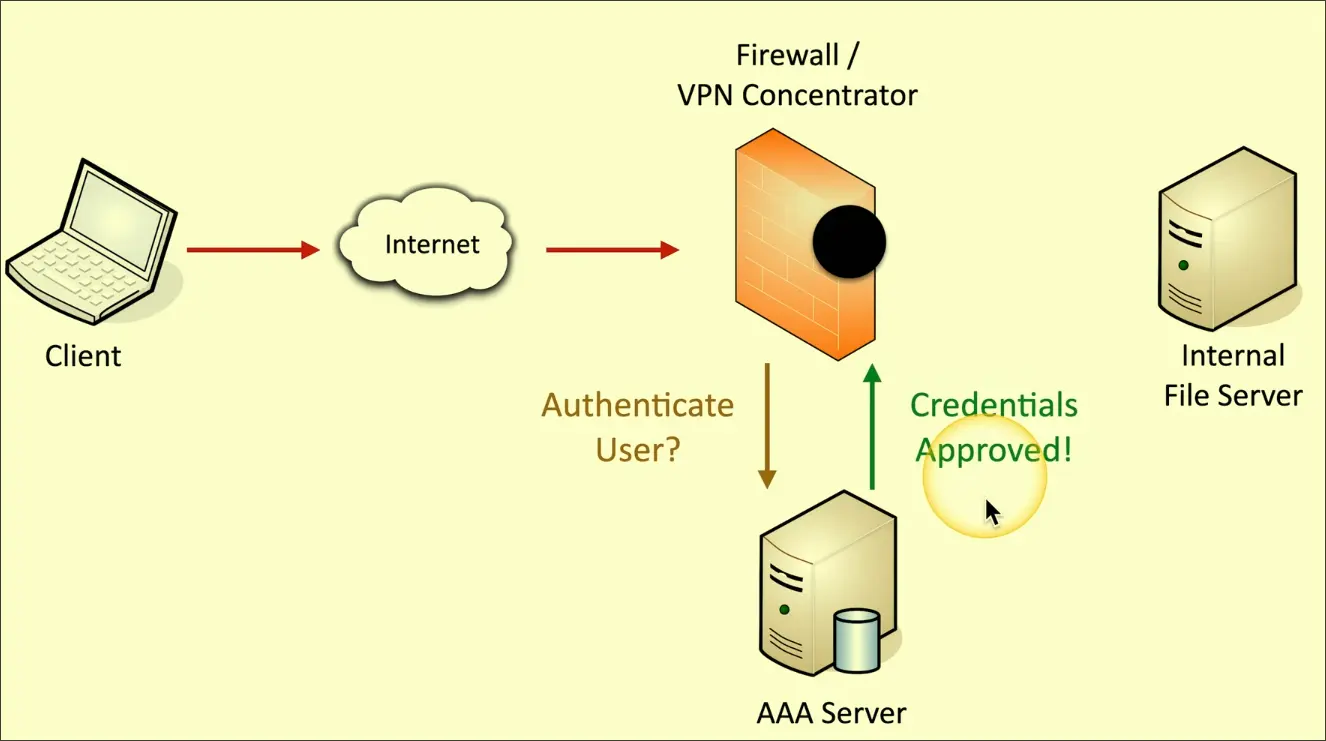
These servers sit on a LAN to provide AAA resources.
