ISSessionsCTF 2025
Challenges
This CTF was great, but to be honest I wish I had gotten some more difficult rev challenges.
Silly Time
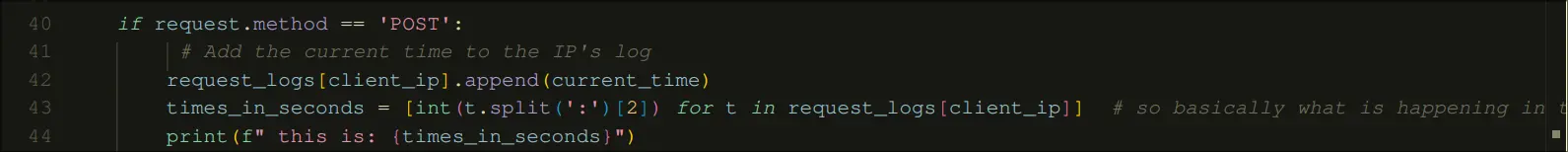 This implementation of time checking is flawed. it only checks the seconds, so if we space out our requests by minutes but have the same final second, then we win
This implementation of time checking is flawed. it only checks the seconds, so if we space out our requests by minutes but have the same final second, then we win
 Look above, this list contains only the seconds.
So, just simply send 5 requests like this:
Look above, this list contains only the seconds.
So, just simply send 5 requests like this:
curl -X POST -F "username=value1" -F "password=value2" https://issessionsctf-sillytime.chals.io/login
And you get this response:
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Login - Shadow Theme</title>
<style>
body {
font-family: Arial, sans-serif;
background-color: #2a2a2a;
color: #f0f0f0;
display: flex;
justify-content: center;
align-items: center;
height: 100vh;
margin: 0;
}
.login-container {
background-color: #333;
padding: rem;
border-radius: 10px;
box-shadow: 0 4px 15px rgba(0, 0, 0, 0.7);
width: 1000px;
text-align: center;
}
.login-container h2 {
margin-bottom: 1.5rem;
color: #ddd;
}
input[type="text"], input[type="password"] {
width: 100%;
padding: 0.5rem;
margin-bottom: 1rem;
border: none;
border-radius: 5px;
box-shadow: inset 0 1px 5px rgba(0, 0, 0, 0.5);
background-color: #444;
color: #f0f0f0;
}
input[type="submit"] {
background-color: #555;
border: none;
padding: 0.7rem;
width: 100%;
border-radius: 5px;
cursor: pointer;
box-shadow: 0 2px 10px rgba(0, 0, 0, 0.4);
color: #f0f0f0;
}
input[type="submit"]:hover {
background-color: #666;
}
.flash-message {
margin-top: 1rem;
color: #ff4f4f;
font-size: 0.9rem;
}
.flash-success {
color: #28a745;
}
</style>
</head>
<body>
<div class="login-container">
<h2>bhbureauCTF{what_4_s1LLy_1mpLemENT4ti0n_of_LOggING-1N}</h2>
</div>
</body>
How Good Are You
I downloaded the pcap and opened it in apackets.com and downloaded the binary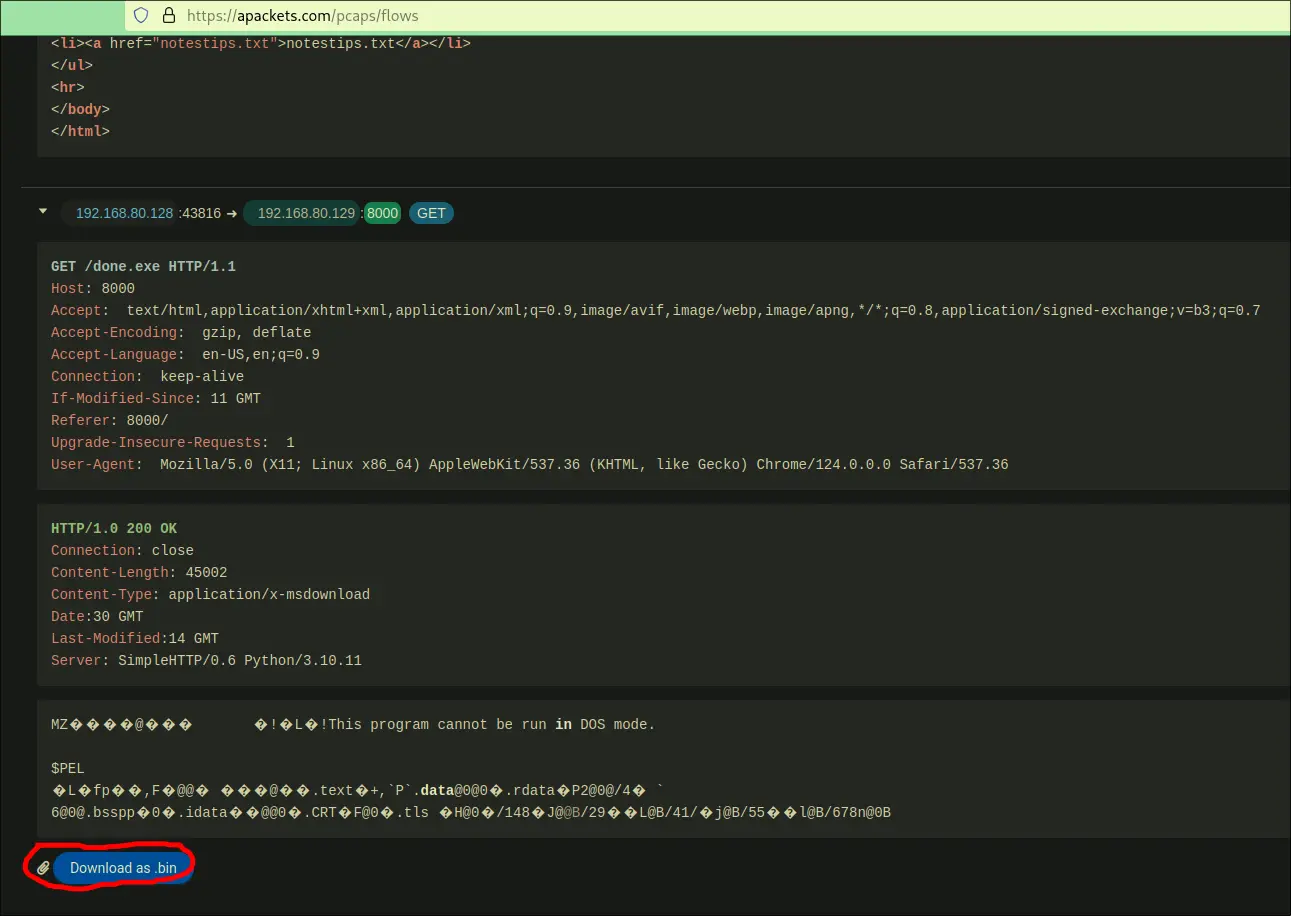 When running, we get this:
When running, we get this:
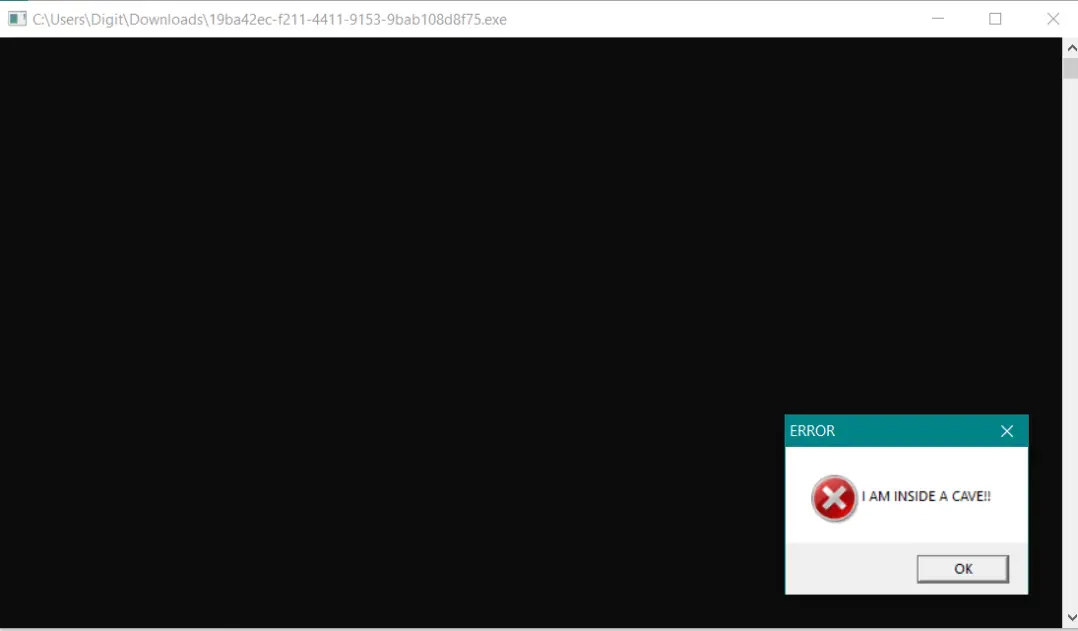
What could this mean? Code Cave?
The First Programming One
This one was just a reverse mapping, here was my script to decode it roughly. I had to choose between which combination to pick. The final string was almost the same except for some space between 'mining' and 'operations'import itertools
message = "fr34rsjlfr3hf53d7r7yrjefr3hrtfr34rsfr3hgtr4fr3hrtf53d7rsjlgtr4rtsf53d7hrfr3hrxfr34f53d7rtsfr3hrxrewfr3hf53d74gfr3hfr34rsjki4f53d7gjerxhbvfr34fr3hfr34rsfr3hrtsfr34gjerxhbvhrf53d7fg4tfr34rsfr3hrxfr3fr3hgtfs5fr34rtsf53d7gjerxhbvf53d7fr34rsjlfr3hf53d7gje3fr3hrxfr34rsjkirts234v5f53d7rtsfr3hrxrewfr3hf53d7gtfs5fr3hrxfr3hrxgtfsf53d7fg4tgtfsgtr4rxhbvfr3hrts234v5f53d7gtfs5fr3hrxfr3hrxgtfsf53d7rewgjerxhbvgjerxhbvhrf53d7fr3hrxfg4tfr3hfr34rsgtr4fr34gjefr3hrxrxhbvrtsf53d7gtr4fr34rsfr34rsfr3hrxfr3hrtrxhbvgtf53d7fr34rsjlfr3hf53d7hrgtfsfr3hrxr7yrjefr3h234v5f53d7gtfs5fr3hrxfr3hrxgtfsf53d7gtfs5gtr4fr34rsrts234v5f53d7gtfs5fr3hrxfr3hrxgtfsf53d7rewgtr4gtfsgje3gtr4fr34rsfr3h234v5f53d7gjef53d7rsjlgtr44gfr3hf53d7rxhbvfr3hrxfr34f53d7r7yrjefr3hfr3hrxhbvf53d7gtr4fr34f53d7fr34rsjlfr3hf53d7r7yrjefr3hrtfr34rsfr3hgtr4fr3hrtf53d74gfr3hfr34rsjki4f53d7gtfsfr3hrxrxhbvhrf53d7gtr4rxhbvgtf53d7gjef53d7gje3fr3hrxrxhbvgtfr3hfr34rsf53d7gje3rsjlgtr4fr34f53d7fr34rsjlfr3hf53d7fg4tgtfsgtr4rxhbvf53d7gjertsf53d7rew34fr3hrxfr34rsf53d7fr34rsjlfr3hf53d7rew34fr3hrtfr34fr3hrtfr34rsfr3hf53d7rsjlfr3hfr34rsfr3h234v5f53d7gjefr34f53d7rtsfr3hfr3hrewrtsf53d7gtfsgjejkifr3hf53d7fr34rsjlfr3hjki4f53d7gtr4fr34rsfr3hf53d7fg4tgtfsgtr4rxhbvrxhbvgjerxhbvhrf53d7rtsfr3hrxrewfr3hfr34rsjlgjerxhbvhrf53d7r7yrjegjehrf53d7gtr4rxhbvgtf53d7gjefr34f53d7rewgtr4jkifr3hrtsf53d7rewfr3hf53d7fr3hrtrxhbvfr3hgtr4rtsjki4f53d7rxhbvfr3hrxfr34f53d7jkirxhbvfr3hrxgje3gjerxhbvhrf53d7gje3rsjlgtr4fr34f53d7gjefr34f53d7gjerts234v5f53d7gjef53d7rew34fr3hgtr4fr34rsf53d7rew34fr3hrxfr34rsf53d7gje3rsjlgtr4fr34f53d7gje3fr3hrxfr3hrtgtfsgtf53d7rsjlgtr4fg4tfg4tfr3hrxhbvf53d7gjerew34f53d7gjef53d7hrfr3hrxfr34f53d7gjerxhbvf53d7fr34rsjlfr3hf53d7gje3gtr4jki4234v5f53d7gjef53d7gtr4rewf53d74gfr3hfr34rsjki4f53d7gtfs5fr3hrxrxhbvrew34fr3hrtrtsfr3hgt"
al6 = {
"fr3hrx":"o",
"fr3hrt":"u",
"fr34rs":"r",
"rxhbv":"n",
"r7yrje":"b",
"gtr4":"a",
"234v5":".",
"f53d7":" ",
"gtfs5":"c",
"rew34":"f",
"fg4t":"p",
"rsjl":"h",
"gje3":"w",
"gje":"i",
"gtfs":"l",
"rew":"m",
"jki4":"y",
"fr34":"t",
"fr3h":"e",
"gt":"d",
"4r":"x",
"4g":"v",
"r7y":"z",
"rts":"s",
"rj":"q",
"hr":"g",
"fr3":"j",
"jki":"k",
}
def substitution_flag(original_message):
keys = [50, 89, 99, 121, 26, 235, 247, 166, 383, 266, 39, 282, 397, 338, 78, 141, 302]
print('bhbureauCTF{', end='')
for sub in keys:
print(message[sub], end='')
print('}')
# decode the message
# split the message by ' ' spaces
segments = message.split("f53d7")
for i in segments:
print(i, end=" ")
#print(segments)
finalmessage = ""
for segment in segments:
print("message is:")
print("-----------")
print(finalmessage)
keyslist = []
for key in list(al6.keys()):
if key in segment:
keyslist.append(key)
userinp = ""
tempmsg = segment
while userinp != 'n':
for i in range(len(keyslist)):
print(f"({i}) : {keyslist[i]} -> {al6[keyslist[i]]}")
print(f"r reset")
print(f"n continue")
print(f"segment is: {tempmsg}")
userinp = input()
if userinp.isdigit():
tempmsg = tempmsg.replace(keyslist[int(userinp)], al6[keyslist[int(userinp)]])
if userinp == 'r':
tempmsg = segment
finalmessage+=tempmsg
print(finalmessage)
The final message ended up being: "the bureau has got some very interesting projects in the works. some cool planes. cool mining operations around the globe. cool cars. cool malware. i have not been at the bureau very long and i wonder what the plan is for the future here. it seems like they are planning something big and it makes me uneasy not knowing what it is. i fear for what would happen if i got in the way. i am very confused" Run it throught the substitution function inside the script and you get the flag
Defusal
The challenge requires POST requests in quick succession. Sending the curl requests through the terminal is enough.curl -X POST -H "Content-Type: application/json" -d '{"wire": "red"}' https://issessionsctf-defusal.chals.io/cut-wire
curl -X POST -H "Content-Type: application/json" -d '{"wire": "green"}' https://issessionsctf-defusal.chals.io/cut-wire
curl -X POST -H "Content-Type: application/json" -d '{"wire": "blue"}' https://issessionsctf-defusal.chals.io/cut-wire
curl -X POST -H "Content-Type: application/json" -d '{"wire": "yellow"}' https://issessionsctf-defusal.chals.io/cut-wire
curl -X POST -H "Content-Type: application/json" -d '{"wire": "orange"}' https://issessionsctf-defusal.chals.io/cut-wire
curl -X POST -H "Content-Type: application/json" -d '{"wire": "purple"}' https://issessionsctf-defusal.chals.io/cut-wire
curl -X POST -H "Content-Type: application/json" -d '{"wire": "cyan"}' https://issessionsctf-defusal.chals.io/cut-wire
curl -X POST -H "Content-Type: application/json" -d '{"wire": "lime"}' https://issessionsctf-defusal.chals.io/cut-wire
curl -X POST https://issessionsctf-defusal.chals.io/open-case

Zettelkasten