UTMSAM & Deerhacks Mini CTF 2025
Challenges
This is a follow-up post to the Deerhacks Hackathon Devlog Halfway through the competition a CTF challenge was given to all participants. A form was sent and our goal was to submit some flags.
We were about finished with out Golang backend when this started and so we had time to start playing this CTF, not that we wouldnt immediately start anyways.
First Challenge
The discord message we were given is as such: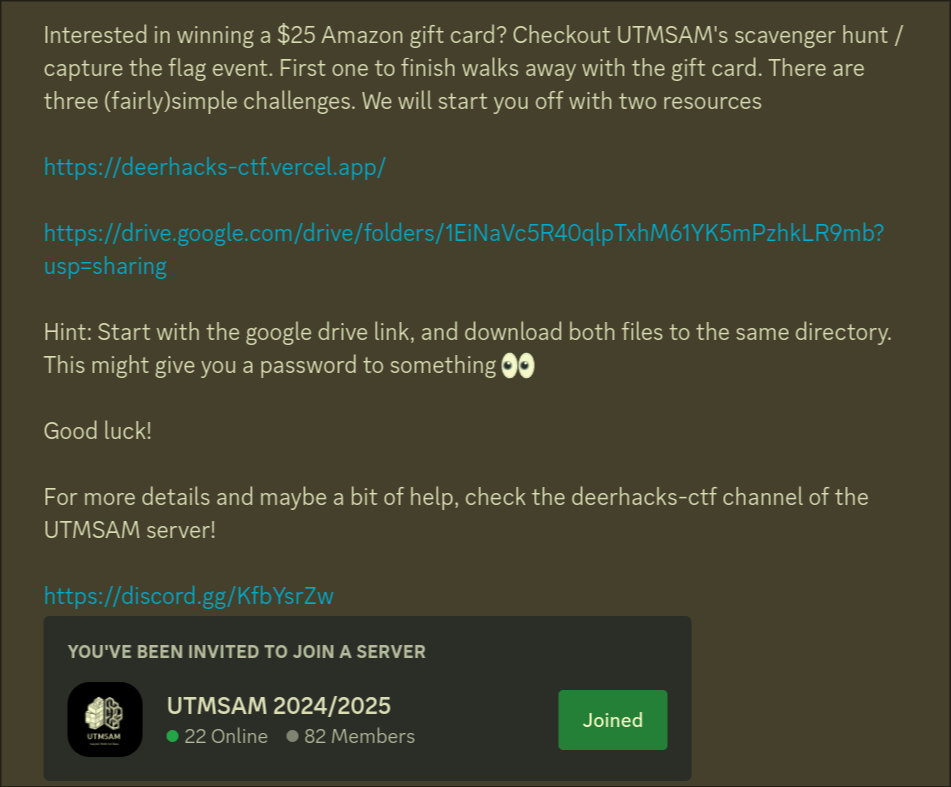
- https://deerhacks-ctf.vercel.app/
- https://drive.google.com/drive/folders/1EiNaVc5R40qlpTxhM61YK5mPzhkLR9mb?usp=sharing
- We need to input a code into the web application. (Note that the web application is offline at the moment)
- The readme is as follows:
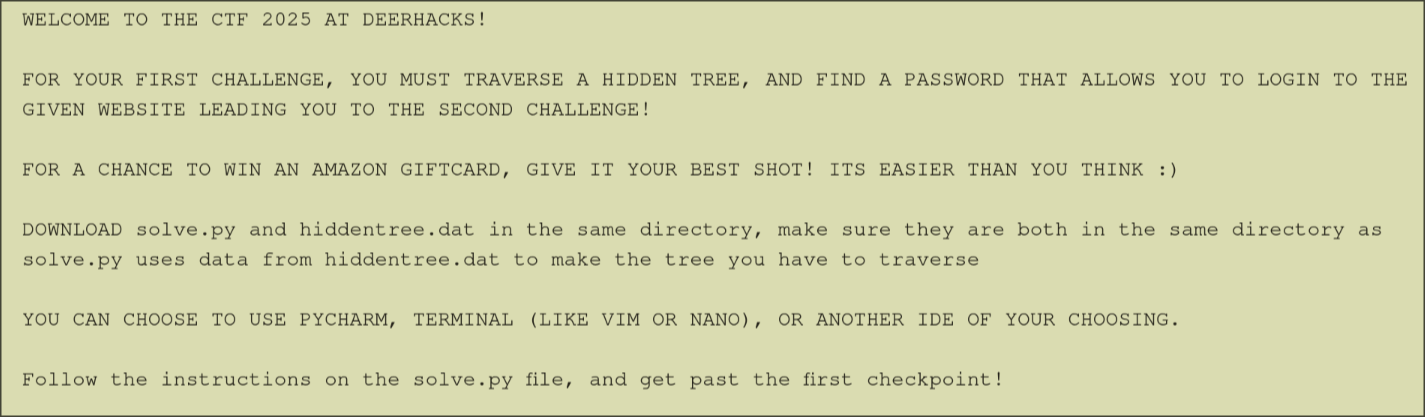
- The python code is searching through a tree until you piece together the flag. with the characters being the values of the nodes.
Our solution was just this:
import base64
import zlib
# Read the encoded .dat file
with open("hiddentree.dat", "rb") as f:
decoded_content = zlib.decompress(base64.b64decode(f.read())).decode()
# Execute the hidden Python code
exec(decoded_content)
# Now you can use the HiddenBinaryTree class
tree = HiddenBinaryTree()
#DO NOT CHANGE ANYTHING BEFORE THIS FUNCTION
def traverse(node):
if node is None:
return
print(node._value, end='') # Print current node's value
traverse(node._left) # Traverse left subtree
traverse(node._right) # Traverse right subtree
if __name__ == "__main__":
traverse(tree.get_root())
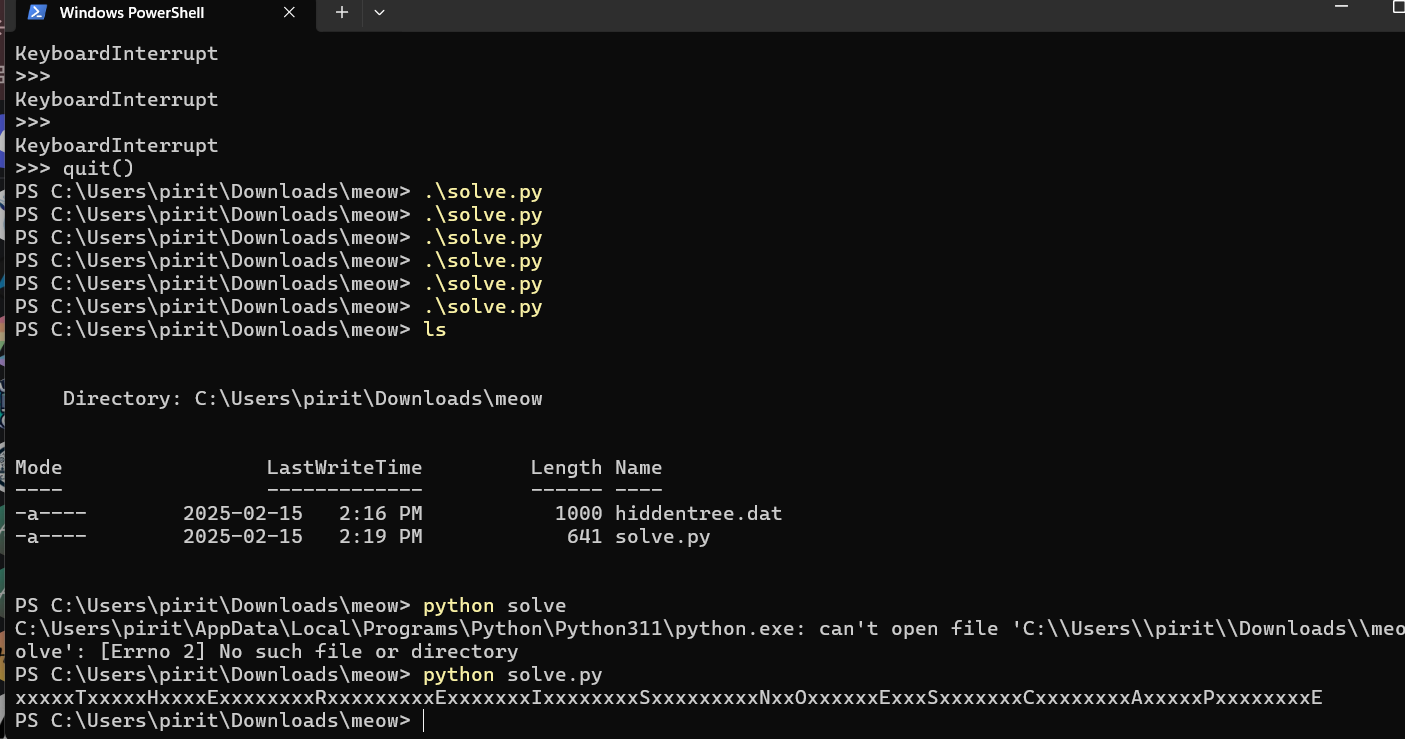
THEREISNOESCAPE is the passcode.
Second Challenge
After inputting the code, you are redirected to a second google drive: https://drive.google.com/drive/folders/1SL30hdH_Z-5A1EAf8aHkk2Wf8zZ24dfuThe challenge description was:
"Look beyond the surface—sometimes the key is in the timestamps, author info, or even hidden comments. Metadata can tell a story the file itself won’t."
We are also given 4 images.
Immediate thing we did was search the metadata with exiftool.
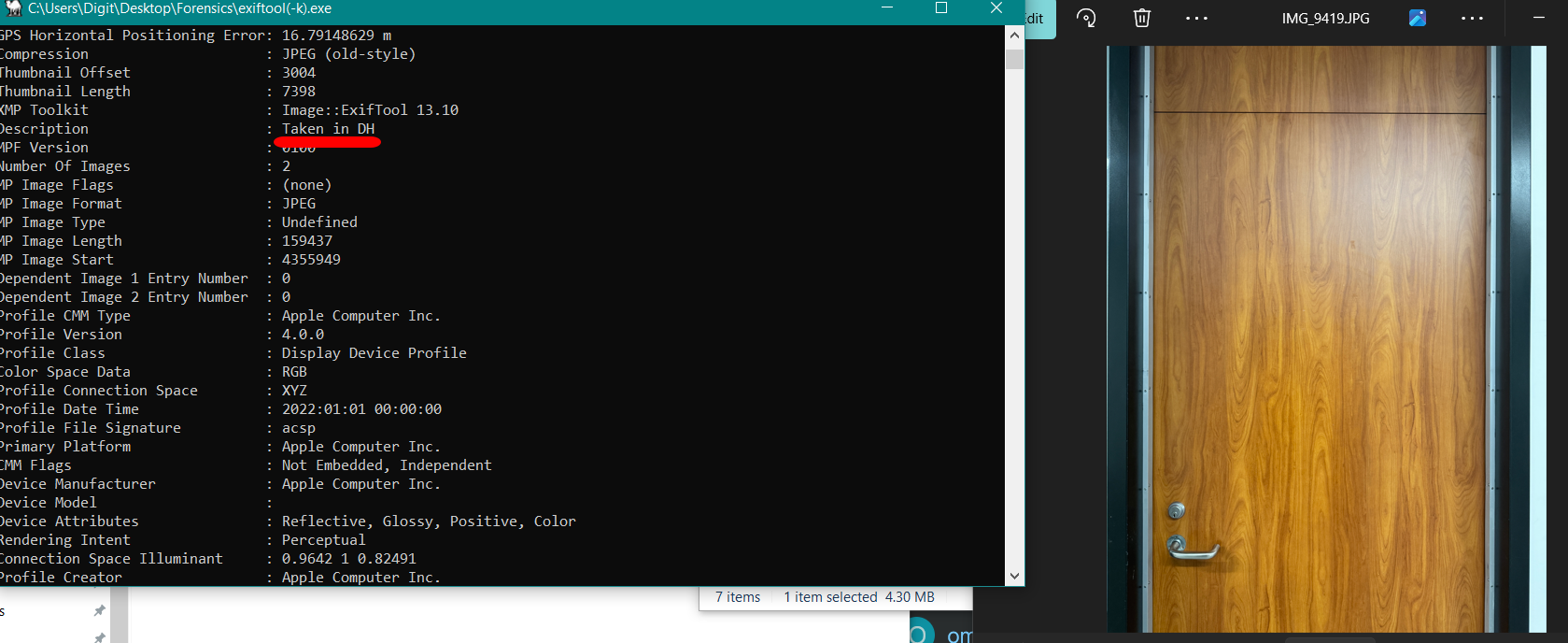
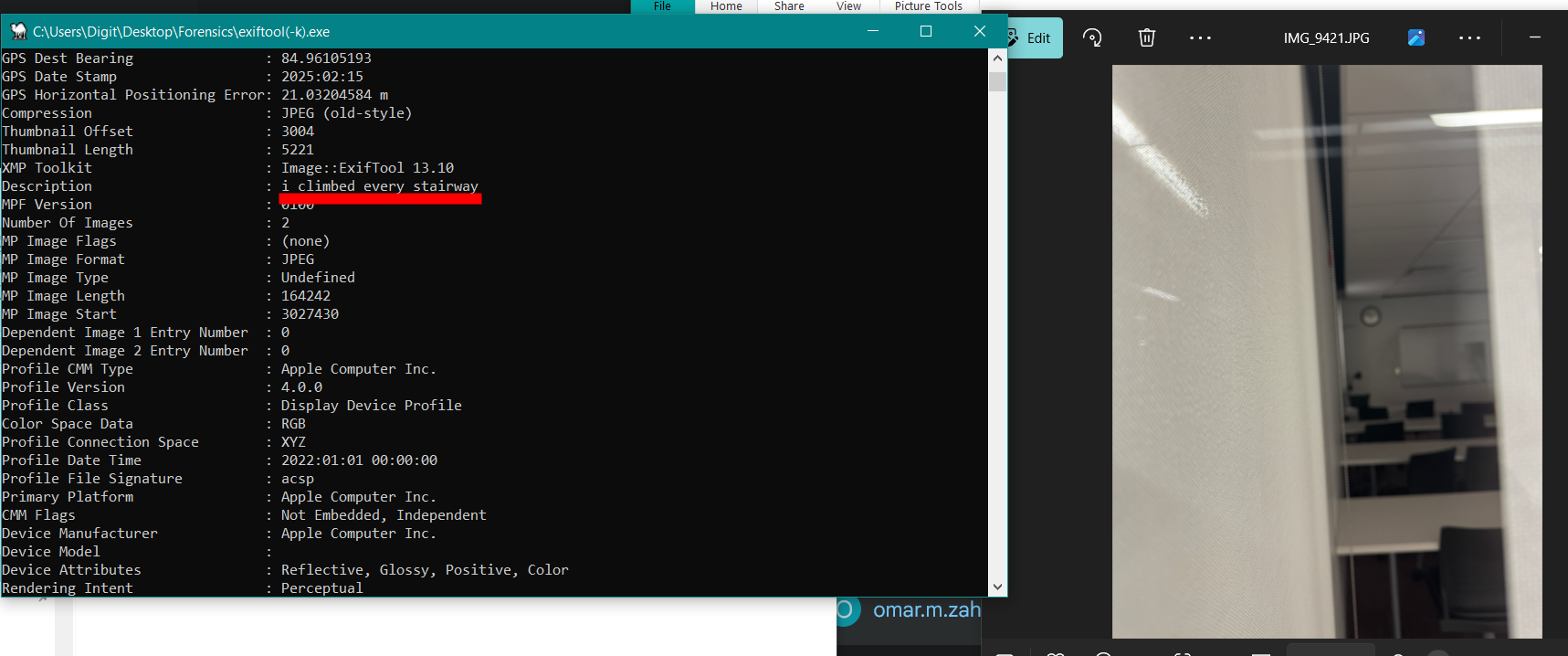
We went up to the highest floor, and we found the exact same fire extinguisher.
 We spent a while searching this place until we found the room, the room had the code on the whiteboard
We spent a while searching this place until we found the room, the room had the code on the whiteboard

Third Challenge
After entering the room, we get this url: https://docs.google.com/forms/d/e/1FAIpQLScWxF1aIaM5jOqVu99Rp6kUvrfRr4GfI3sIgMwVHL-wRK2zVA/viewformThe last challenge was to fill out a google form After running some test cases, we get the following inputs fail:
- First one: []
- Second one: [1,1]
- Third one: [5,3,1]
And afterwards we wait for human confirmation that those were the right codes.

Zettelkasten